Hey guys it’s Yash Again, Today we are going to learn about the Importance of Subdomain enumeration; Ya Ya I know that many of you know how to perform subdomain BUT Do You know how to perform sub-domain Enumeration IN DEPTH, Today I Am Talking About Hidden way of subdomain enumeration that Top Bug Bounty Hunter USE In there Sub-domain Enumeration Part. with Best Wordlists Out There
So Let’s Get Started Bug Bounty Hunters

Common Ways of finding subdomains using tools. so I am not going to Explain all the things But today I’ll cover only the IMPORTANT thing that I think New bug bounty hunters should know
The top tools that I think bug bounty hunters should use 1st is Our favourite is Amass and Subfinder so I am not going to spend a lot of time explaining these tools i will provide their commands below You can use the help menu to understand these flags/commands
amass enum -passive -norecursive -noalts -d yashsec.com -o Output.txt
subfinder -d yashsec.com -v -t 25 -o subfinder.txt
I Use these flags/commands while using these tools
IN−DEPTH
So now the main part of the story In-Depth Approach
How many of you know the OneForAll, A Powerful Chinese Subdomain Enumeration Tool
OneforAll tool is a Killer tool for finding sub-domains You can read this tool information Here & Also You Can Download This Tool using the following command
git clone https://github.com/shmilylty/OneForAll.git ; cd OneForAll/ ; python3 -m pip install -U pip setuptools wheel ; pip3 install -r requirements.txt ; python3 oneforall.py --help
Just keep in mind that → python3 should be at least a version 3.8.0 and pip3 at least version 19.2.2.
Subdomain Brute Forcing
I think many people know how to brute force sub-domains. In this blog, I am going to share the tools that I use in the sub-domain brute forcing, wordlists, and best wordlists according to me. Using those wordlists I get unique sub-domains that are Not tested.
Tools
for sub-domain brute-forcing I use the PureDNS tool command will be provided below. for more information, you can read This
Wordlists
I use SecLists, FuzzDB And You Can use this AssetNote wordlists. I want to highlight this best-dns-wordlist.txt and make sure to use this file for sub-domain brute forcing.
Try Lots of different wordlists for brute forcing. Using this method you will find a lot of unique sub-domains After Getting most of the sub-domains try to find the sub-domain takeover.
puredns bruteforce ~/w/SecLists/Discovery/DNS/dns-Jhaddix.txt $domain -r ~/w/purednsResolvers/resolvers.txt >> puredns2.txt
You can use this file as a Resolver
Also i have lots of Other methods too we will discus them in another blog post happy Hunting All 🎔 & also i don’t want to make this blog big so.
POC
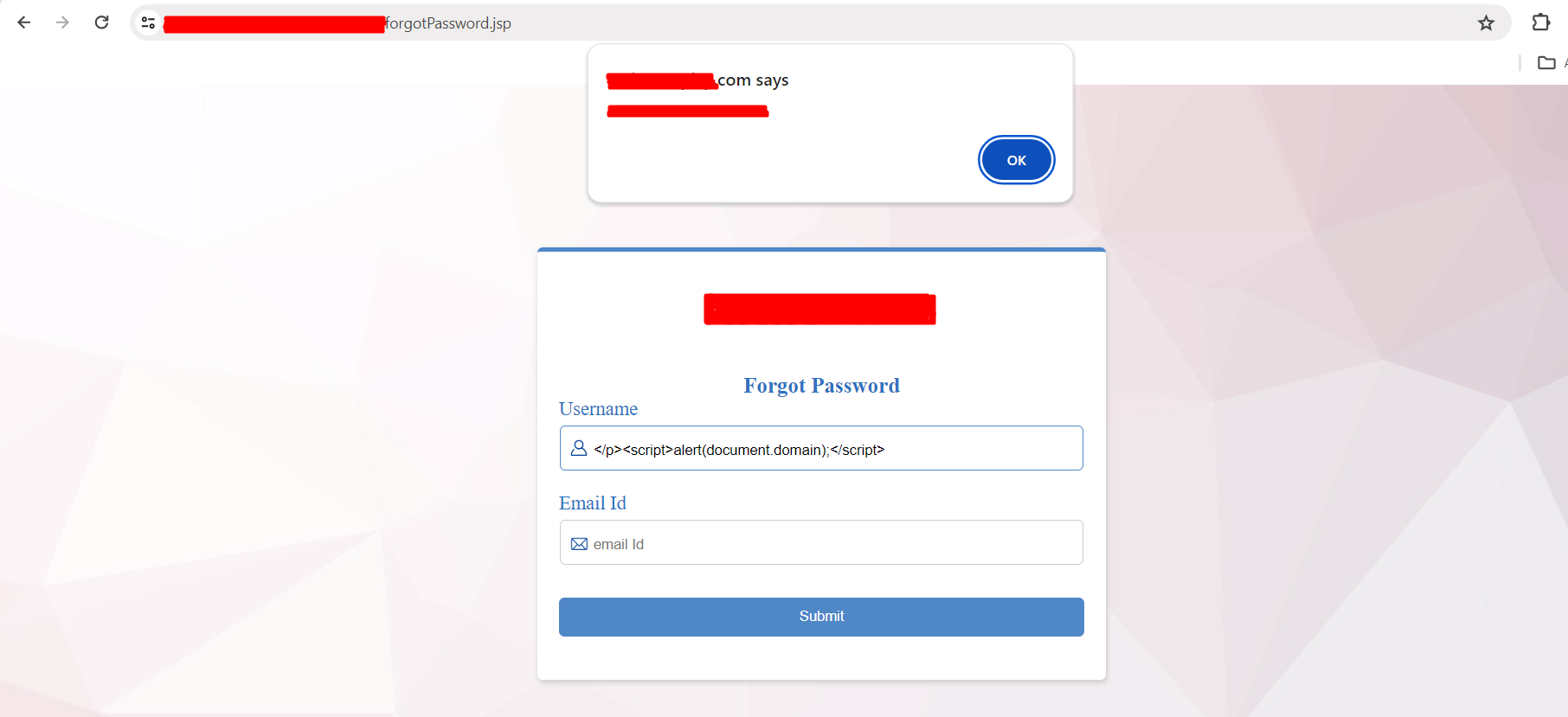
Using above listed method i am able to find some cool bugs like SQL Injection, Reflected XSS and Sensitive information disclosure.
Recap
- We talk about the best wordlists for sub-domain Brute forcing with wordlists
- Best tool for sub-domain Brute forcing with commands
- A unique tool for finding sub-domains.
I am going to write more blogs about Bug Bounty Hunting and wapt so Make Sure to
visit Yash Security for such amazing blog posts.
Thank You ❟❛❟