Hii its Yash Gurav from Pune, India.
I am a B.Com student with a 2-year passion for cybersecurity and bug bounties. I confess i underestimated the power of Google dorking. But let me tell you, once I harnessed its potential, the game changed.
In this blog we are going to see the importance of the google dorking with example and resources.
I am able to find XSS and SQL Injection using following google dork
site:*.*.gov.in inurl:?idYou can also use ext:php or aspx and keep in mind you can also change the id keyword to the most common parameters that are vulnereble to xss
This experience opened my eyes to the immense power of Google dorking. It’s not just about finding vulnerabilities, it’s about being resourceful, creative, and using the tools at your disposal to make a real impact.
Bug Bounty tip : Always check for ALL possibilities
After reporting this issue, I was searching for more bugs then i tried SQL Injection for the same parameter.
Boom ! !
POC
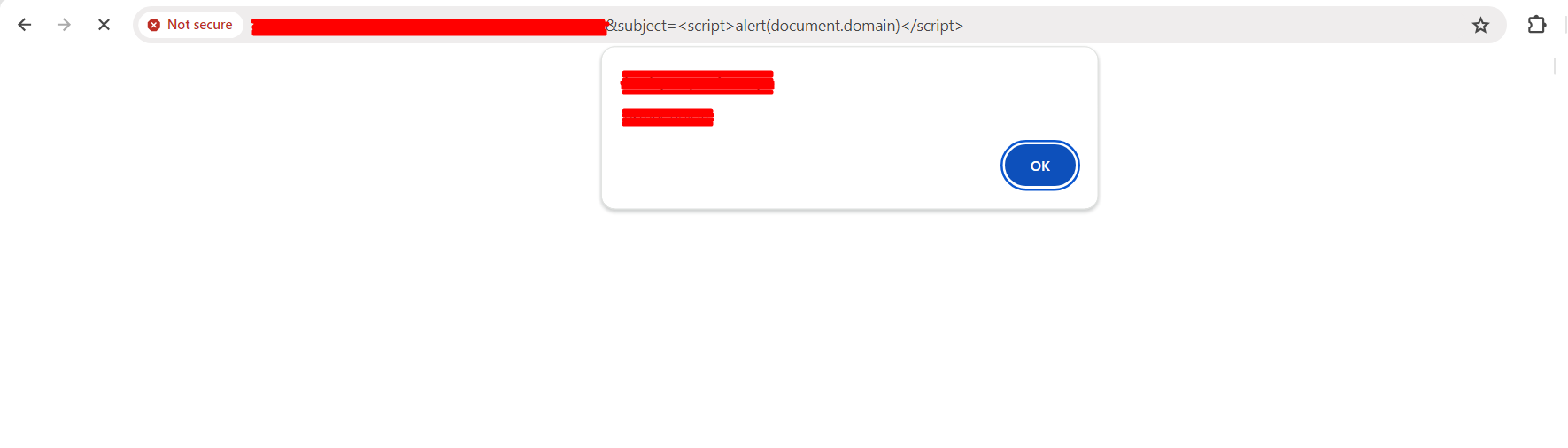
it works and i was able to find 2 bugs 1st is Relfected XSS and 2nd one is SQL Injection.
You can use the following google dorks while hunting on the bug bounty program or wapt Enjoy ;D
/2wayvideochat/index.php?r=
/elms/subscribe.php?course_id=
/gen_confirm.php?errmsg=
/hexjector.php?site=
/index.php?option=com_easygb&Itemid=
/index.php?view=help&faq=1&ref=
/index.php?view=help&faq=1&ref=
/info.asp?page=fullstory&key=1&news_type=news&onvan=
/info.asp?page=fullstory&key=1&news_type=news&onvan=
/main.php?sid=
/news.php?id=
/notice.php?msg=
/preaspjobboard//Employee/emp_login.asp?msg1=
/Property-Cpanel.html?pid=
/schoolmv2/html/studentmain.php?session=
/search.php?search_keywords=
/ser/parohija.php?id=
/showproperty.php?id=
/site_search.php?sfunction=
/strane/pas.php?id=
/vehicle/buy_do_search/?order_direction=
/view.php?PID=
/winners.php?year=2008&type=
/winners.php?year=2008&type=
index.php?option=com_reservations&task=askope&nidser=2&namser=
index.php?option=com_reservations&task=askope&nidser=2&namser=
intext:”Website
inurl:”.php?author=”
inurl:”.php?cat=”
inurl:”.php?cmd=”
inurl:”.php?feedback=”
inurl:”.php?file=”
inurl:”.php?from=”
inurl:”.php?keyword=”
inurl:”.php?mail=”
inurl:”.php?max=”
inurl:”.php?pass=”
inurl:”.php?pass=”
inurl:”.php?q=”
inurl:”.php?query=”
inurl:”.php?search=”
inurl:”.php?searchstring=”
inurl:”.php?searchstring=”
inurl:”.php?tag=”
inurl:”.php?txt=”
inurl:”.php?vote=”
inurl:”.php?years=”
inurl:”.php?z=”
inurl:”contentPage.php?id=”
inurl:”displayResource.php?id=”
inurl:.com/search.asp
inurl:/poll/default.asp?catid=
inurl:/products/classified/headersearch.php?sid=
inurl:/products/orkutclone/scrapbook.php?id=
inurl:/search_results.php?search=
inurl:/search_results.php?search=
inurl:/search_results.php?search=Search&k=
inurl:/search_results.php?search=Search&k=
inurl:”contentPage.php?id=”
inurl:”displayResource.php?id=”
inurl:com_feedpostold/feedpost.php?url=
inurl:headersearch.php?sid=
inurl:scrapbook.php?id=
inurl:search.php?q=
pages/match_report.php?mid=
Thank for reading blog if you want to know how to the top bug bounty hunter do the sub domain recon you can find that blog HERE