What is 2fa?
2fa is known as 2-factor authentication and more than 90% of applications have this feature and it helps users to improve their account security on web applications and mobile applications. The most used method that the application uses to get the 2fa is code/OTP.
Most applications send 6 or 4-digit OTP on the mobile number to verify the user. The application can send some kind of code or any alphanumeric strings. then, the user needs to fill in the code in a certain time period then they can access their account
2fa bypass methods.
Log in to your web application/mobile application and enable the 2fa feautre before testing
So Let’s dive in

Response code manipulation
- Navigate to the login panel. Enter the correct username and password, and the Application will send you the OTP code.
- Enter any arbitrary code and intercept the HTTP request using a proxy tool such as burpsuite and send it into the repeater tab. Observe the application response, if the response is like the following code
(“success”: false, “Another-Parameters”: “value”) # false for the wrong OTP
(“success”: true, “Another-Parameters”: “value”) # true for the Right OTPIn response if {“success”: false, “Another-Parameters”: “value”} change it to {“success”: true, “Another-Parameters”: “value”}
In response if {“success”: false, “Another-Parameters”: “value”} change it to {“success”: true, “Another-Parameters”: “value”}
Status code manipulation
After putting the wrong OTP you might get 401 Unauthorized then change it to 200 OK
OTP code leak in response
Sometimes what happens if you put the wrong OTP in the HTTP response application leak the correct OTP then you can use the correct OTP in your second attempt
POC
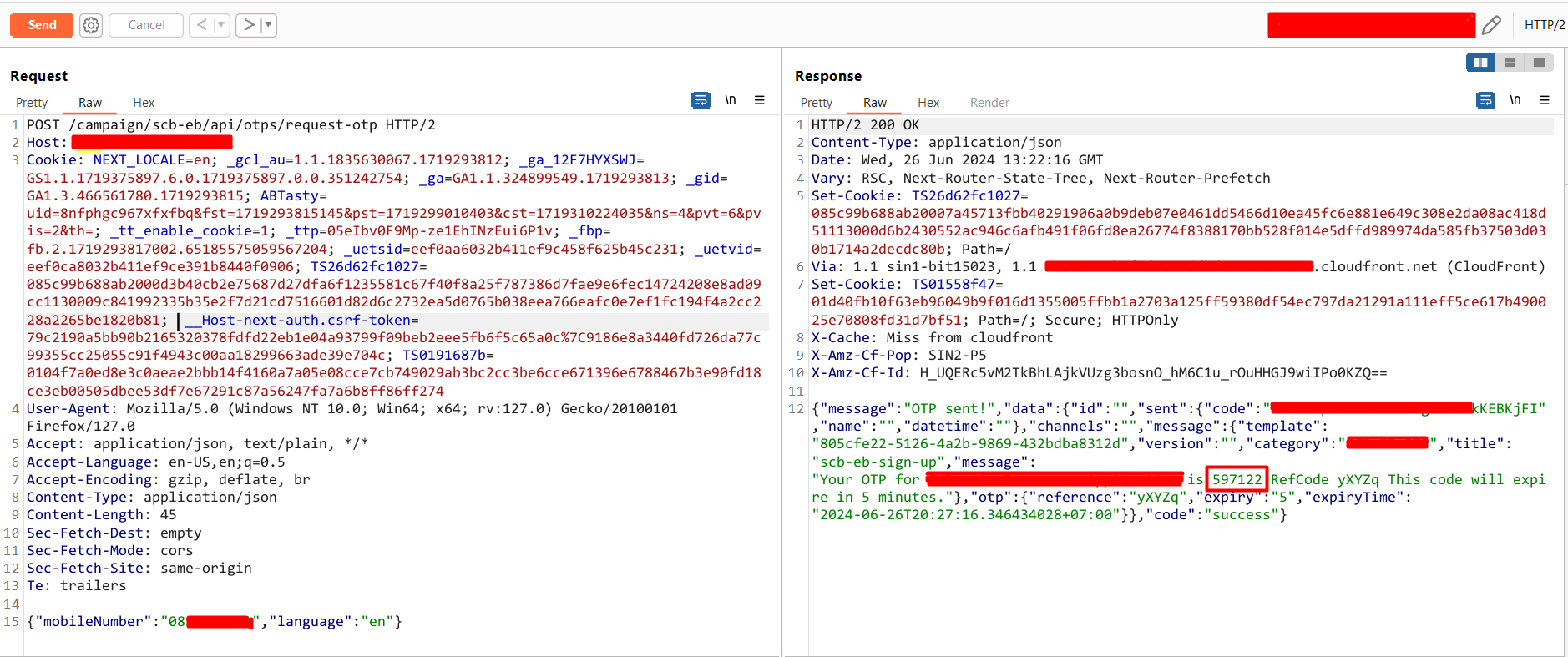
No Rate Limit OTP
If there is no rate limit on the OTP brute-forcing then you can brute-force OTP following methods.
- Log in to your application and enter the wrong OTP
- Intercept the HTTP request using a proxy tool such as Burp Suite and send it into an intruder tab.
- Select the attack type as a “Sniper” and set the OTP as a position. Navigate to “Payloads” and set the payload type according to your site mostly it is “Numbers” and From “000000” to “999999” step always be “1” [If your application accepts only 4 digit OTP then instead of 000000 you can choose 0000]
Missing 2fa code integrity
Suppose you have 2 User accounts then you have enabled the 2fa for both accounts and you can use the 1st User account OTP to log in to the 2nd User account.
2fa disable via forgot password feature
This method is one of the best methods to bypass the 2-factor authentication. You can do the forgot password and set the new password. if you can log in to your account without entering the 2fa that means you have successfully bypassed the 2fa
Boom !!
Try the most common methods
- Enter the most common OTPs such as 000000, 0000
- Enter null instead of the OTP
- Remove the OTP value as well as the parameter and send the request.
Forced browsing/Direct Endpoint access
- Log in to your application with valid credentials
- Enter the correct OTP and not down the endpoint where the application redirects us after a successful login
- Log out from the account and again log in to your account with valid credentials when an application asks you to enter the OTP then you can put the endpoint you copied in step 2 and wait to see.
Using OAuth [Open Authorization}
This method is only applicable when an application has a OAuth feature such as Log in with google and facebook
- First, log in to your web application/mobile application using the common email ID and enable the 2fa.
- Log out from your account and log in to your account using OAuth such as Google, Facebook
Race condition exploitation
you can use the race condition to bypass the 2fa.
Using some headers
You can try some headers to bypass the 2fa code. X-Forwarded-Host header with localhost IP might work, you can try this method to bypass the 2fa.
JS file
This method is rare but you can try, some JS files contain info about the 2fa code.
CSRF on disabling 2fa
if there is no CSRF token then you can try the CSRF attack to disable the 2fa.
Enabling 2fa doesn’t expire previous active sessions
Log in to your web application in 2 different browsers in the same account enable the 2fa feature in one browser and observe that the 2nd browser should log you out and end its session if the session continues and you can do some tasks then it’s a bug.
Backup code abuse
You can bypass 2fa by abusing the backup code feature. Use the above-mentioned methods to bypass the backup code feature to remove/reset 2fa
I have listed all the methods that you can try when hunting/testing on a web app/mobile app.
When I was working on my VAPT project I found that the OTP feature is vulnerable to many attacks such as Brute-Force attacks, OTP leaks in HTTP response and OTP bypass using Response manipulation.
If you like this blog then You can read Master Subdomain HUNTING | Art of Finding Hidden Assets as well I have mentioned some hidden ways to do the sub-domain enumeration for finding fresh targets that have not been tested and you will find some good bugs.
I am going to write more blogs about Bug Bounty Hunting and WAPT so Make Sure to
visit Yash Security for such amazing blog posts.
Thank You ❟❛❟