Hii Everyone!!
Today we are going to learn about the Shodan Dorking and how you can utilize it for getting misconfiguration devices. for your bug bounty hunting.
So let’s get started
Top 10 Shodan Dorks!!
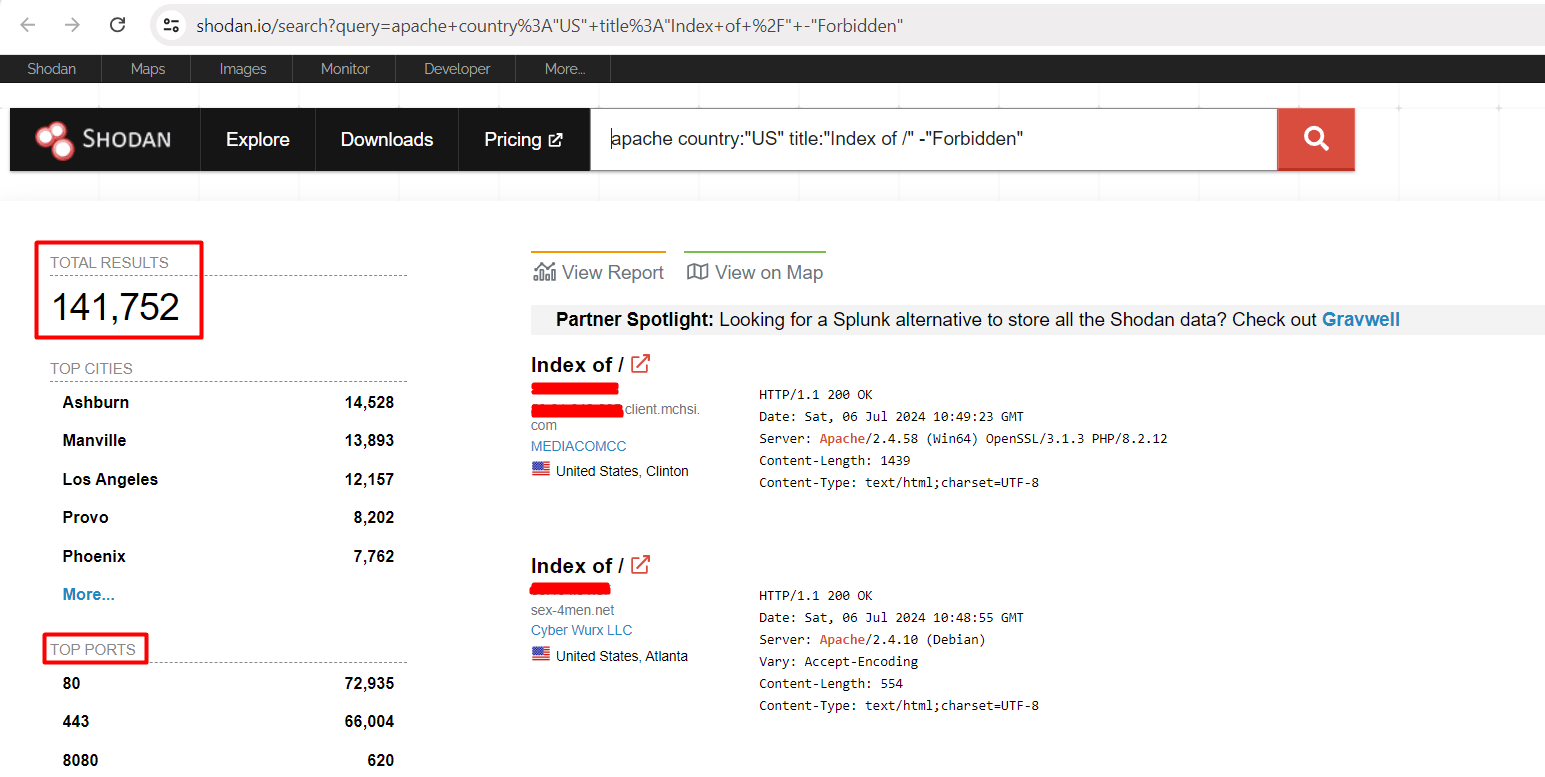
This dork will help you find the default Apache Page
apache country:"YOUR_COUNTRY_CODE" title:"Index of /" -"Forbidden"I have added the POC as well
This dork will help you to find the default login pages
"login:" "password" country:"YOUR_COUNTRY_CODE"Open Elasticsearch Instances
port:9200 country:"YOUR_COUNTRY_CODE"Exposed MongoDB Databases
port:27017 country:"YOUR_COUNTRY_CODE"Misconfigured Jenkins Instances
"http.title:Dashboard" "jenkins country:YOUR_COUNTRY_CODE"Unsecured VNC
"RFB 003.003" port:5900 country:"YOUR_COUNTRY_CODE"Open RDP (Remote Desktop Protocol) Services
port:3389 country:"YOUR_COUNTRY_CODE"Exposed Redis Instances
port:6379 country:"YOUR_COUNTRY_CODE"Insecure FTP Servers
port:21 country:"YOUR_COUNTRY_CODE"Misconfigured Apache Tomcat
"Apache Tomcat" country:"YOUR_COUNTRY_CODE"Just make sure to replace ‘YOUR_COUNTRY_CODE’ with the specific country code to narrow down results to your target region. Please use these search terms responsibly and ensure you follow bug bounty program guidelines while conducting your research.
Happy Hunting!
Reference
Thank You for reading if you like this one then you can also read this Hacking Indian Government with reflected XSS and SQL Injection