Table of Contents
Description of CVE-2024-40711 | UnAuth RCE In Veeam BackUP and Republication Software.
According to NVD,
Deserializing an untrusted data vulnerability with a malicious payload can allow unauthenticated remote code execution (RCE).
Reconnaissance of CVE-2024-40711 | UnAuth RCE In Veeam BackUP and Republication Software.
In this section, we are using online OSINT-based tools to discover the affected domains and IP Addresses.Shodan.io
Shodan.io
Veeam
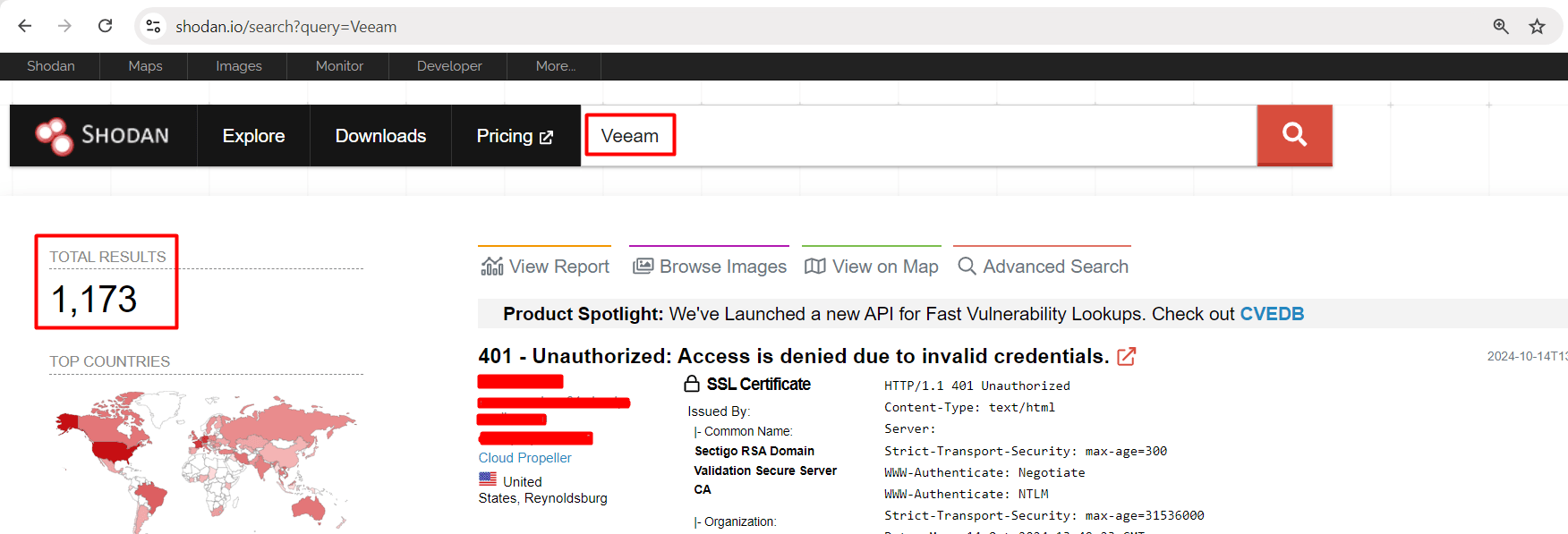
You can use this simple dork to find all the IPs that use Veeam. But if you want to narrow it down more specifically then You can use the following dorks.
Veeam BackupVeeam Backup Enterprise Manager
But in this case, shodan doesn’t have many results then you can use other OSINT tools. that I have listed 😉
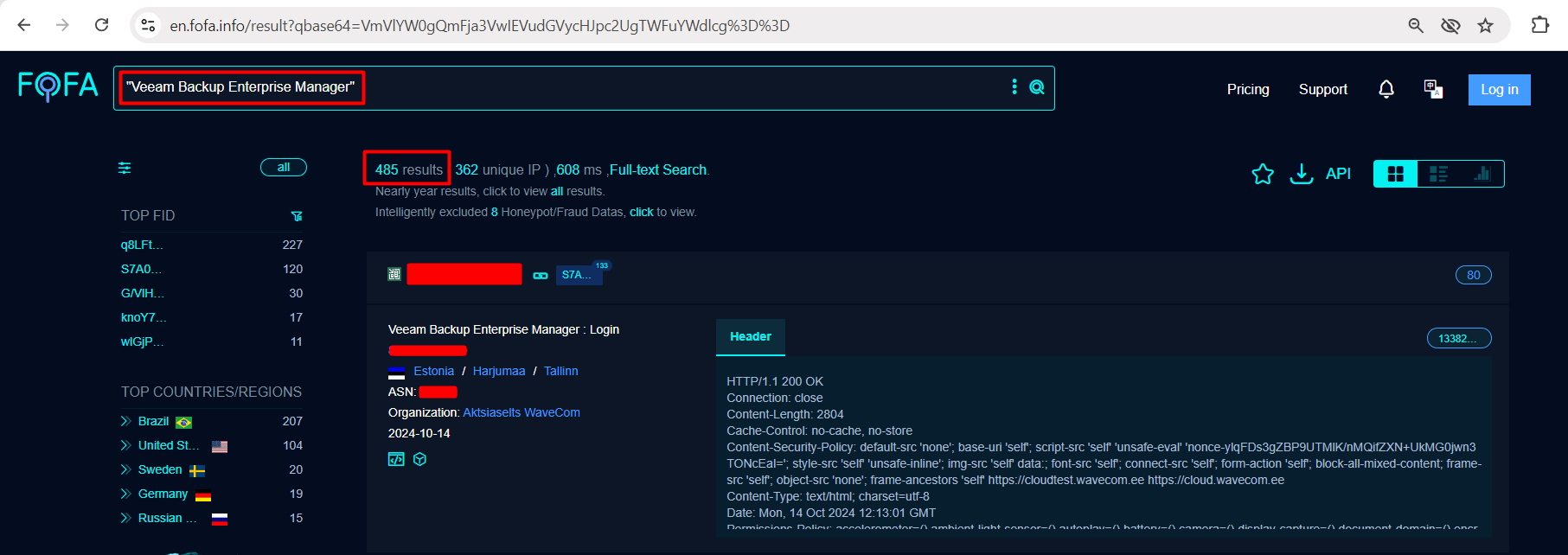
Fofa.info
You can use the following fofa dork to discover the IPs that might be vulnerable to CVE-2024-40711 (RCE In Veeam)
"Veeam Backup Enterprise Manager"
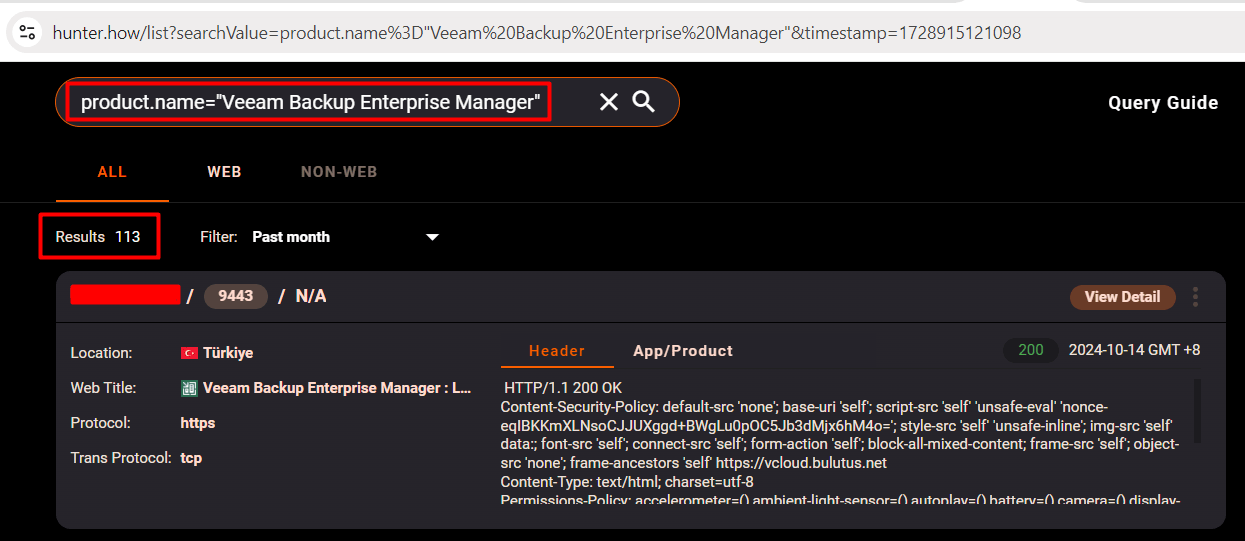
Hunter.how
You can use the following Hunter.how dork to discover the IPs that might be vulnerable to CVE-2024-40711 (RCE In Veeam).
product.name="Veeam Backup Enterprise Manager"
ZoomEYE.HK
You can use the following zoomeye dork to discover the IPs that might be vulnerable to CVE-2024-40711 (RCE In Veeam).
app:"Veeam backup Enterprise Manager"
CVE-2024-40711 Exploit | UnAuth RCE In Veeam BackUp and Software POC
CVE-2024-40711 Github Exploit | RCE In Veeam POC
for More detaisl You can read this BLOG
Impact of CVE-2024-40711 | UnAuth RCE in Veeam BackUp and Republication software.
UnAuthenticated RCE in Veeam backup and republication software (CVE-2024-40711) can be significat impact on CIA (Confidentiality, Intigrity and Availablitiy) on server. By using this CVE-2024-40711 Attacker can perform Criticle tasks such as.
- As Name suggest an attacker can gain full control fo the server via RCE
- An attacker can Modify or delete the PII Information available on Server.
- DATA BREACH: An attacer can access the PII information available on server and it can leads to data breach.
The vulnerability arises from the deserialization of untrusted data, which enables attackers to execute arbitrary code remotely without any user interaction or privileges.
Sevarity of CVE-2024-40711 | UnAuth RCE in Veeam BackUp and Republication Software.
- CVSS: Criticle 9.8
- Vector String:
CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
Remediation of CVE-2024-40711 | UnAuth RCE in Veeam BackUp and Republication software.
- Update the Veeam BackUP and Republication To Version 12.2 or Higher.