Hii Guys,
This Master subdomain HUNTING Part 2 is the 2nd part of Master Subdomain HUNTING | Art of finding Hidden Assets blog post.
Overview
In this part 2 we will be covering the common tools that you can use before going to do “Advance mode in subdomain enumeration” like brute forcing with PureDNS.
What You’ll Learn
- Common subdomain enumeration tools
- Overiew
- Installation
- commands
Amass
About Amass
The OWASP Amass Project performs network mapping of attack surfaces and external asset discovery using open source information gathering and active reconnaissance techniques. – According to there github repository.
In My Words
This tool is one of the best tool for subdomain enumeration. While doing bug bounty hunting or wapt don’t miss to use this tool.
Installation of Amass in Homebrew, DragonFly BSD, FreeBSD, Kali Linux/ Ubuntu/WSL and etc.
Install Amass In Homebrew
brew tap owasp-amass/amass
brew install amassInstall Amass In DragonFly BSD
pkg upgrade
pkg install amassInstall Amass In FreeBSD
cd /usr/ports/dns/amass/ && make install clean
pkg install amassInstall Amass In Kali Linux / Ubuntu
sudo apt-get update ; sudo apt-get install amass
Install Amass In Parrot Linux
apt-get update
apt-get install amassInstall Amass In Pentoo Linux
sudo emerge net-analyzer/amass
# Periodically, execute the following command to update all packages
sudo pentoo-updaterCheck out this official Amass Installation Guide.
Amass commands
# Passive way
amass enum -passive -d google.com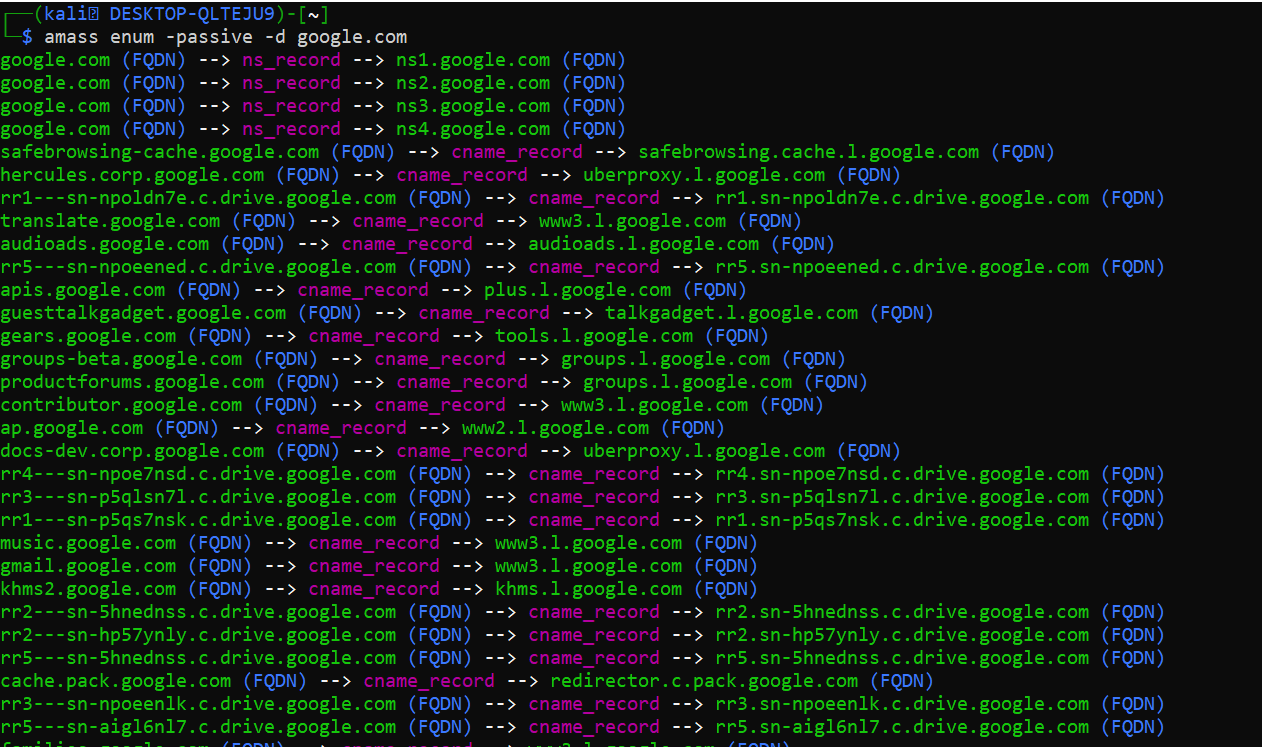
# Active way
amass enum -d google.com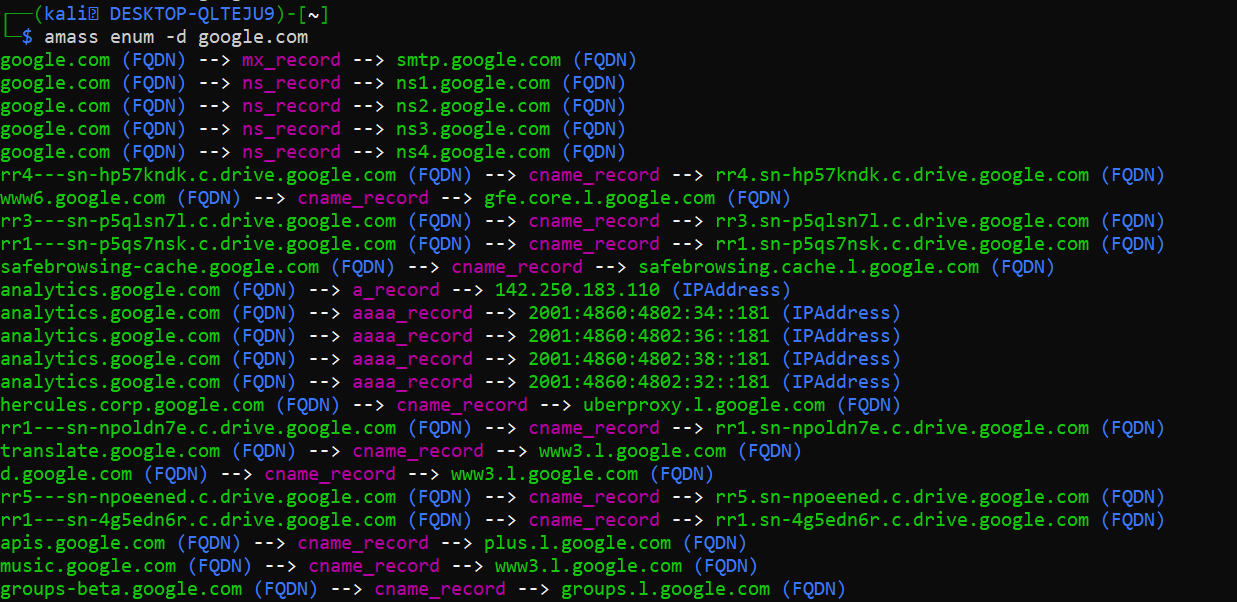
Subfinder
About Subfinder
subfinder is a subdomain discovery tool that returns valid subdomains for websites, using passive online sources. It has a simple, modular architecture and is optimized for speed. subfinder is built for doing one thing only – passive subdomain enumeration, and it does that very well. – According to there github repository
In my words
Its an passive subdomain enumeration tool created by ProjectDiscovery. Project Discovery is an open-source software company that is simplifying security operations for hackers and developers. They are also the creator of nuclei tool.
Installation of Subfinder in Kali Linux/ Ubuntu/WSL
sudo apt install golang ; go install -v github.com/projectdiscovery/subfinder/v2/cmd/subfinder@latest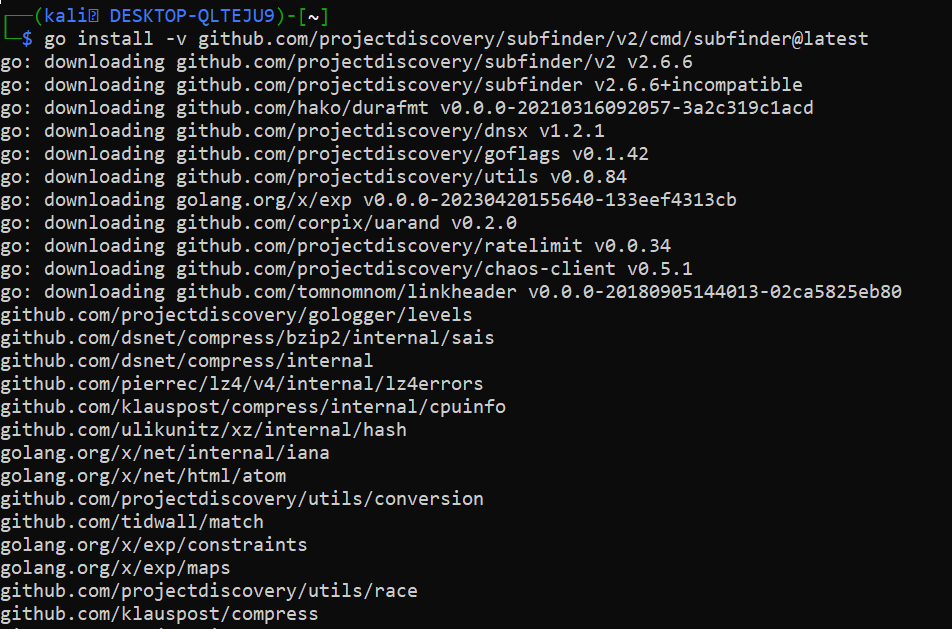
Crate an alias by using the following command
Bash
echo "alias subfinder=~/go/bin/subfinder" >> ~/.bashrc ; source ~/.bashrc ; subfinder -h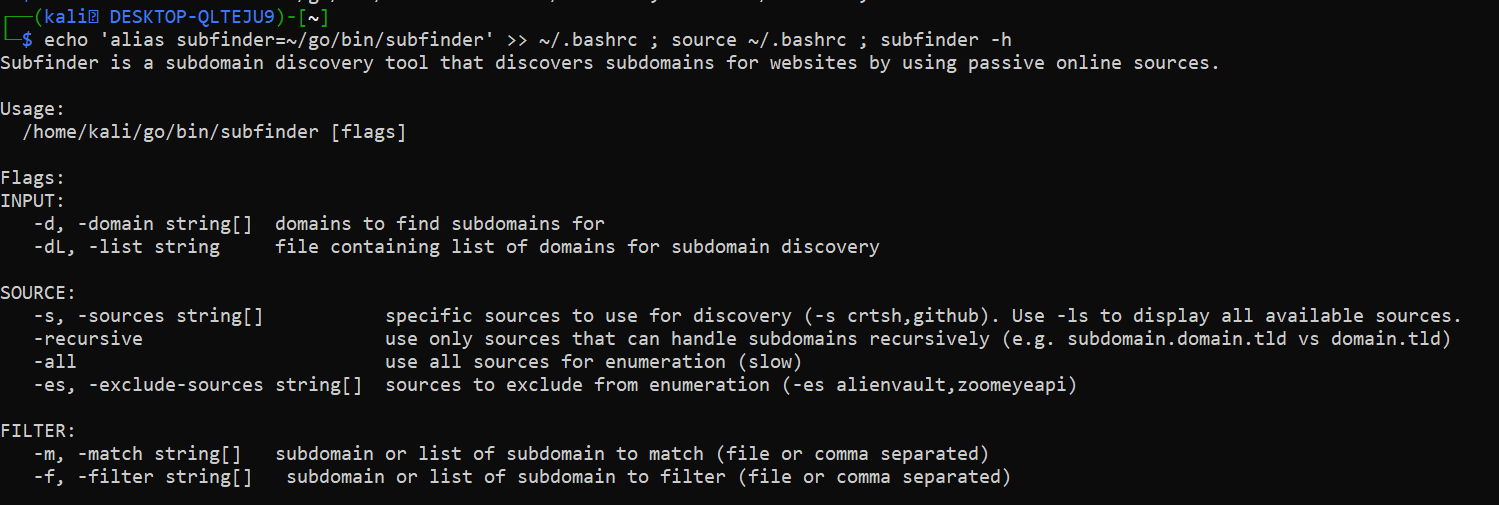
Zsh
echo "alias subfinder=~/go/bin/subfinder" >> ~/.zshrc ; source ~/.zshrc ; subfinder -hSubfinder Command
subfinder -d google.com 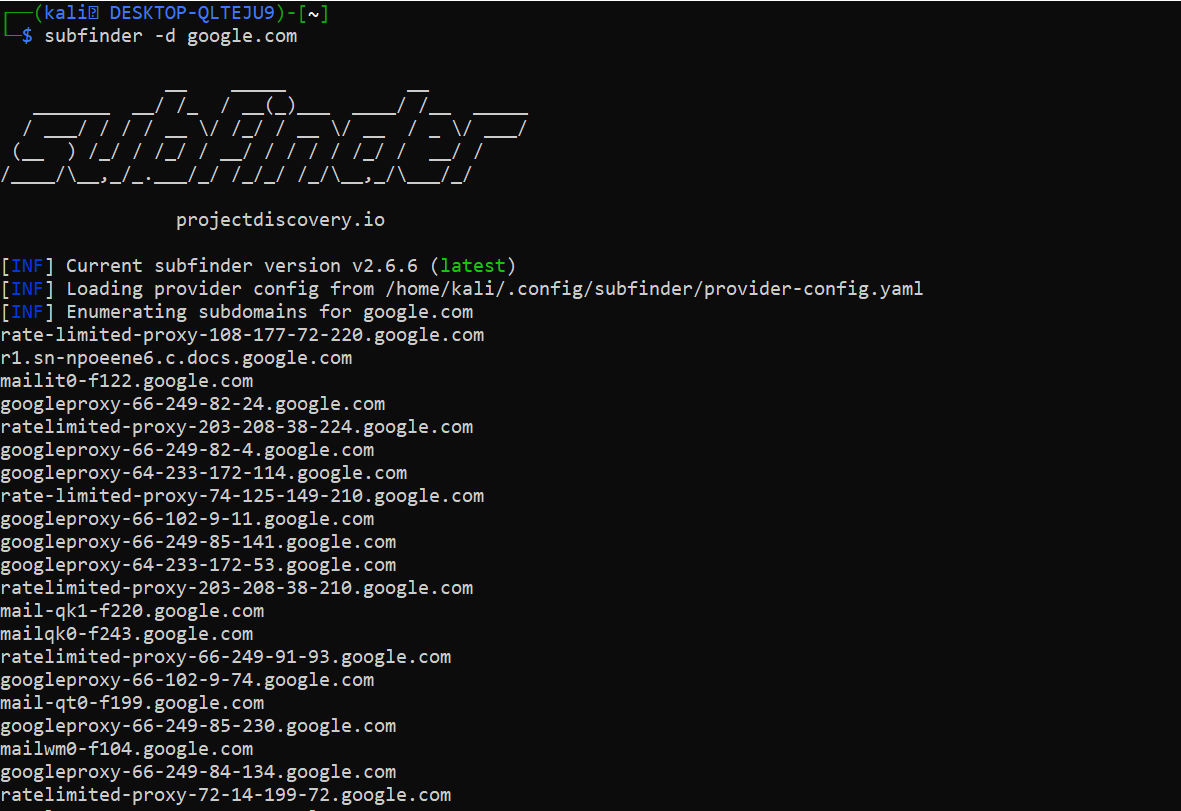
Sublist3r
About Sublist3r
Sublist3r is a python tool designed to enumerate subdomains of websites using OSINT. It helps pentesters and bug hunters collect and gather subdomains for the domain they are targeting. Sublist3r enumerates subdomains using many search engines such as Google, Yahoo, Bing, Baidu and Ask. Sublist3r also enumerates subdomains using Netcraft, Virustotal, ThreatCrowd, DNSdumpster and ReverseDNS. – According to there github repository
In My Words
This tool usese the online search engines for subdomain enumeration search engine like google, yahoo, bing, etc. and also enumerate subdomains using netcraft, virustotal, DNSdumpster and reverseDNS etc.
Installation of Sublist3r in Kali Linux/ Ubuntu/WSL
git clone https://github.com/aboul3la/Sublist3r.git ; cd Sublist3r ; sudo pip install -r requirements.txt ; python3 sublist3r.py -h 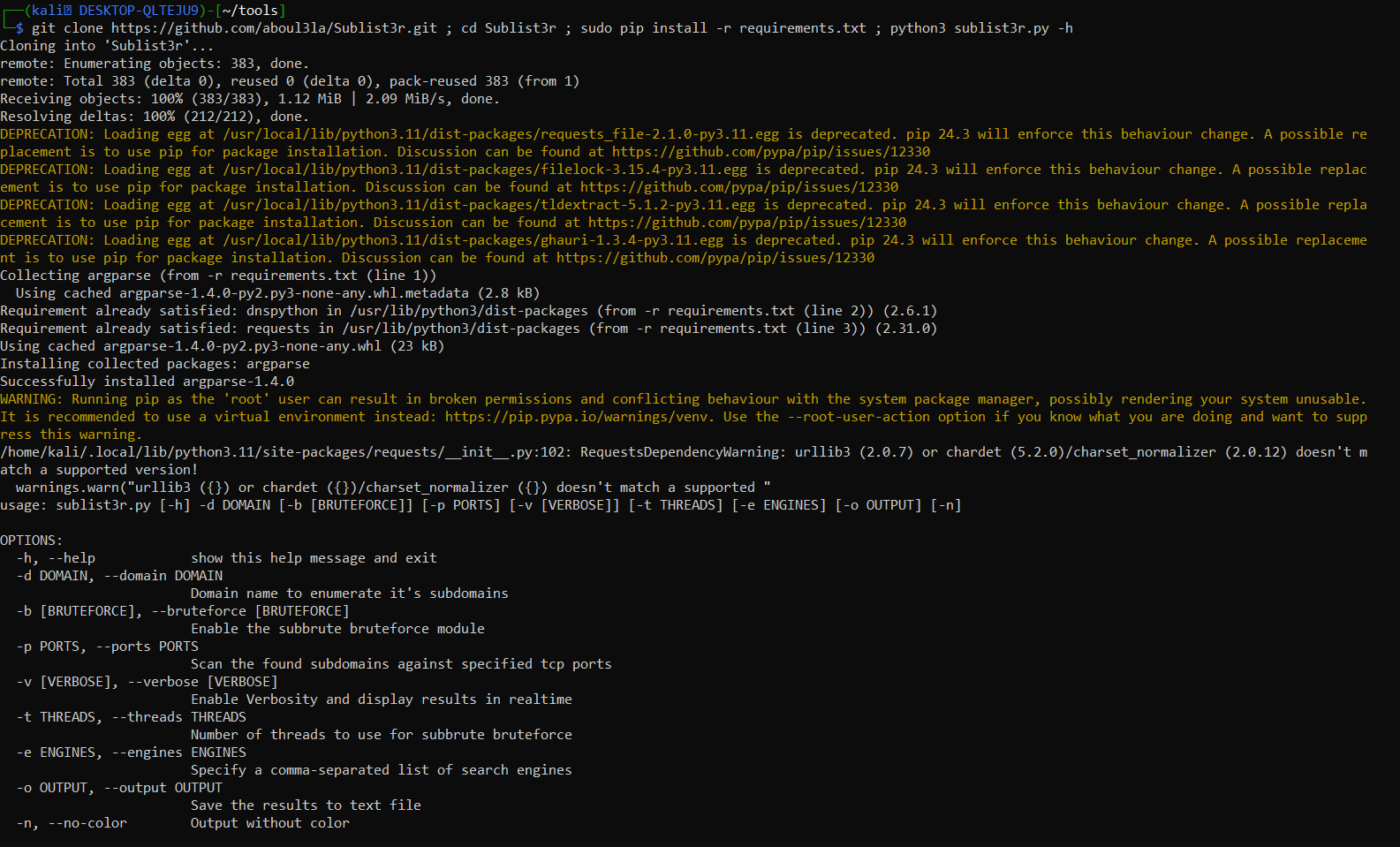
Sublist3r Command
python3 sublist3r.py -d google.com -v -t 25 -o sublist3r_output.txt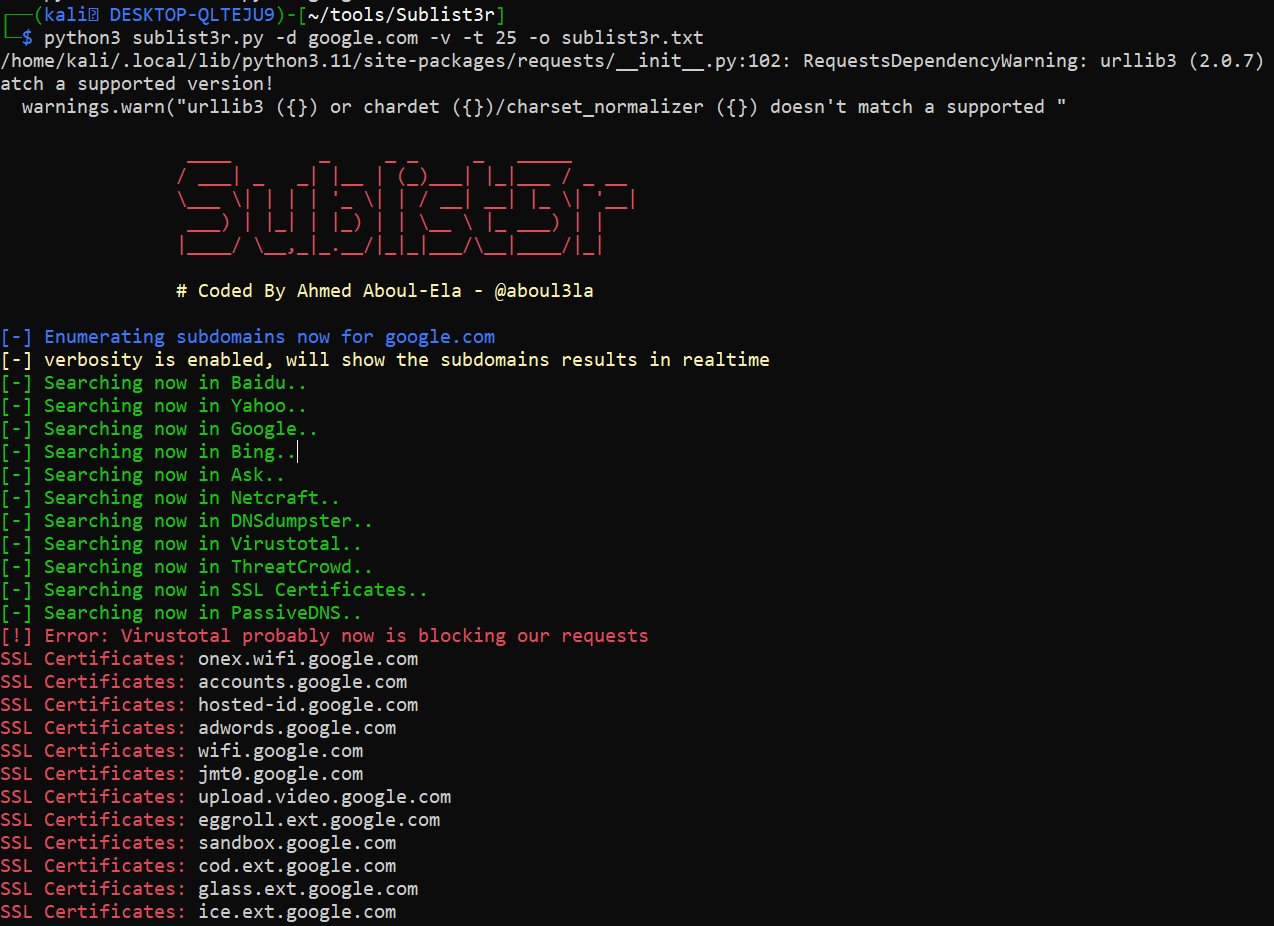
Findomain
Installation of Findomain in Kali Linux/ Ubuntu/WSL
You can check out this Findomain Installation Guide
Findomain commands
# simple command for subdomain enumeration using findomain tool.
findomain -t example.com
# simple command with saving output.
findomain -t example.com -u example.txt
# resolvable subdomains.
findomain -t example.com -r
# resolvable subdomains with output.
findomain -t example.com -r -u example.txt
# Enumerating sub-domains from provided domains list.
findomain -f file_with_domains.txt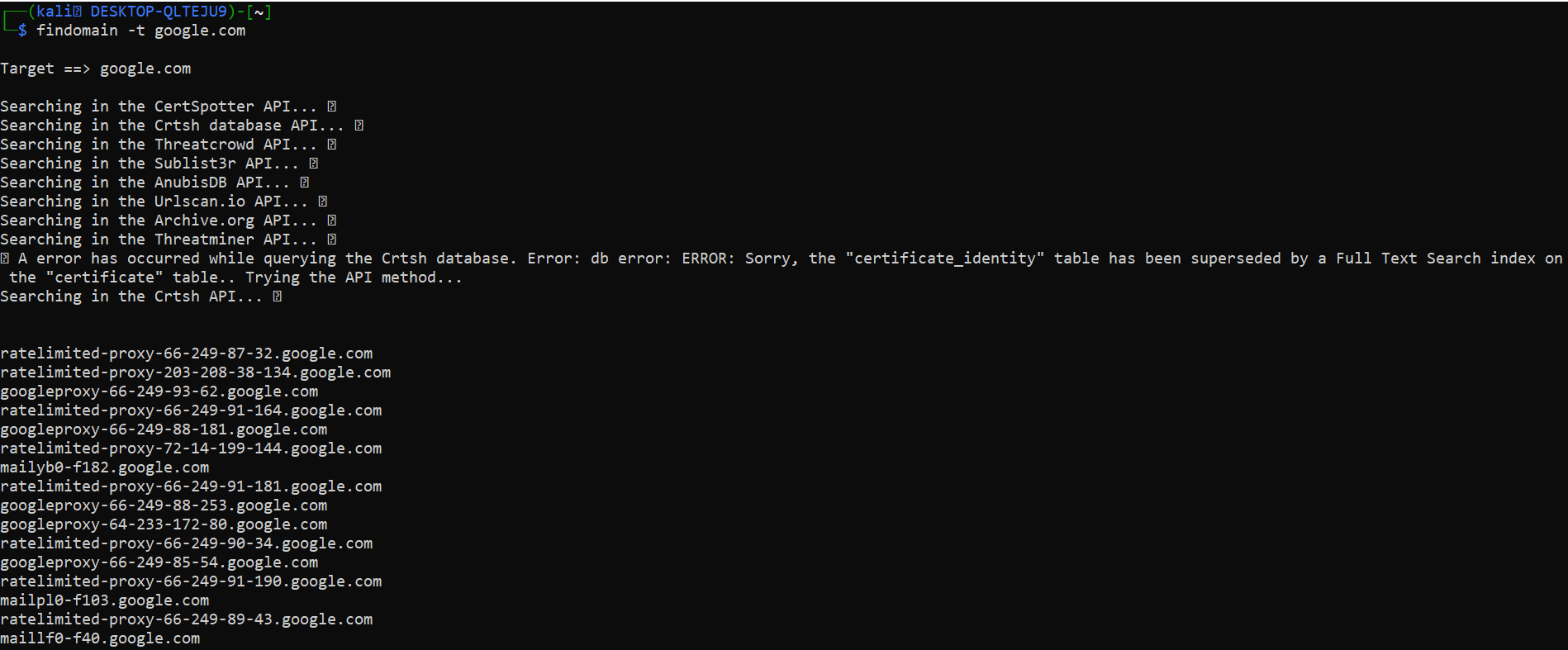
Assetfinder
About Assetfinder
Find domains and subdomains potentially related to a given domain. – According to there github repository
In My Words
Its an simple and Quick subdomain enumeration tool with simple to use. Written in go language (Golang) so its a lot faster tool as compare to other subdomain enumeration tools.
Installation of Assetfinder in Kali Linux/Ubuntu/WSL
sudo apt install golang ; go install github.com/tomnomnom/assetfinder@latest ; ~/go/bin/assetfinder -h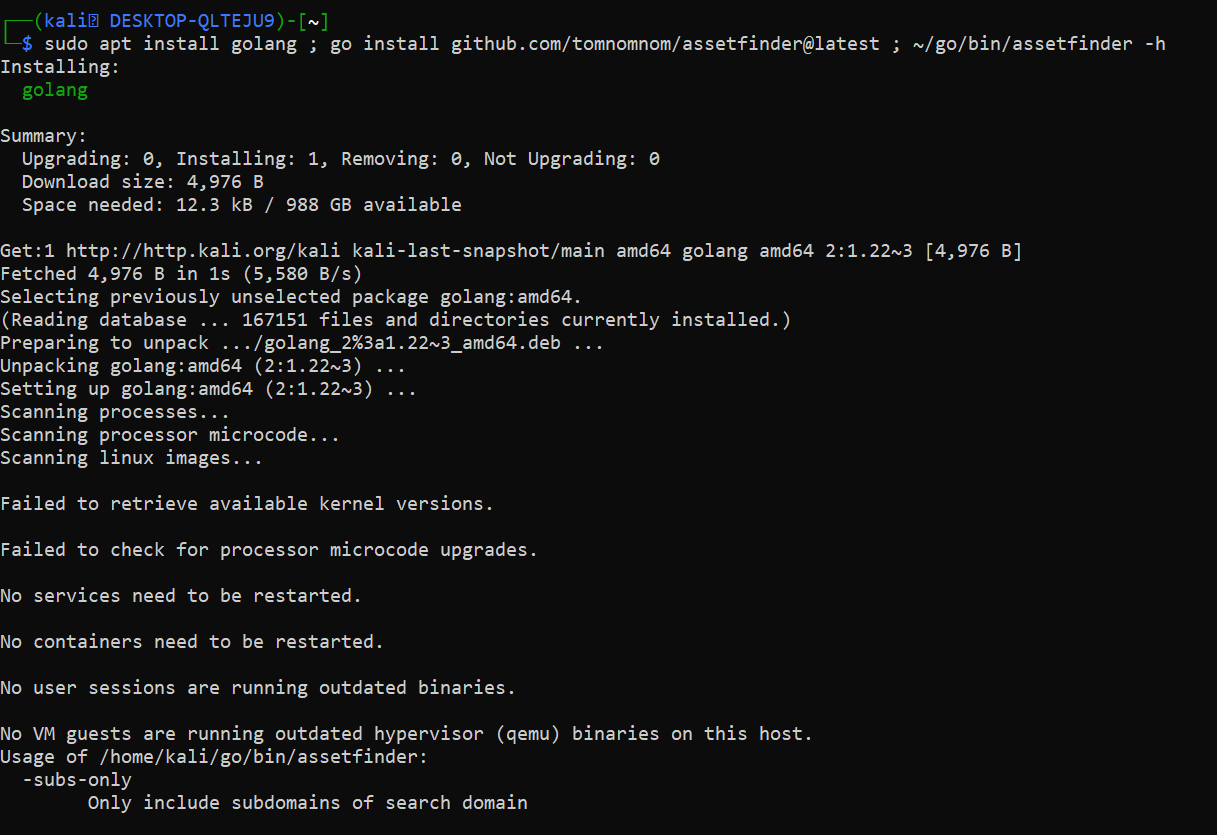
Assetfinder will install in ~/go/bin/ directory you can create a symbolic link by using the following command.
sudo ln -s $HOME/go/bin/assetfinder /usr/local/bin/assetfinderIf above method is not working in your kali linux/ubuntu/WSL then create an alias by using following methods.
Find out which shell is your kali linux/ubuntu/WSL is using bash or zsh.
Bash
echo 'alias assetfinder=~/go/bin/assetfinder' >> ~/.bashrc ; source ~/.bashrc ; assetfinder -h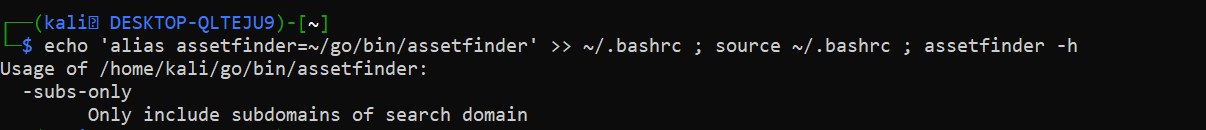
Zsh
echo 'alias assetfinder=~/go/bin/assetfinder' >> ~/.zshrc ; source ~/.zshrc ; assetfinder -hAssetfinder command
assetfinder -subs-only google.com | tee assetfinder_output.txt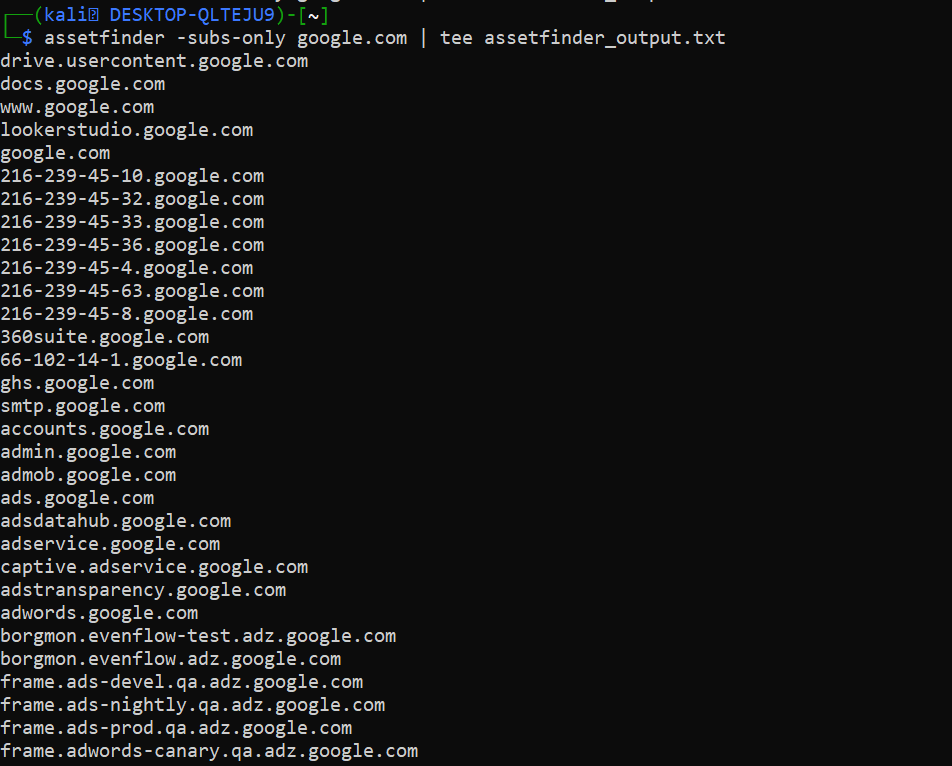
CRT.sh
About CRT.sh
Its an website for subdomain enumeration. Crt.sh website allows user to search for SSL/TLS certificates for a specific domain.
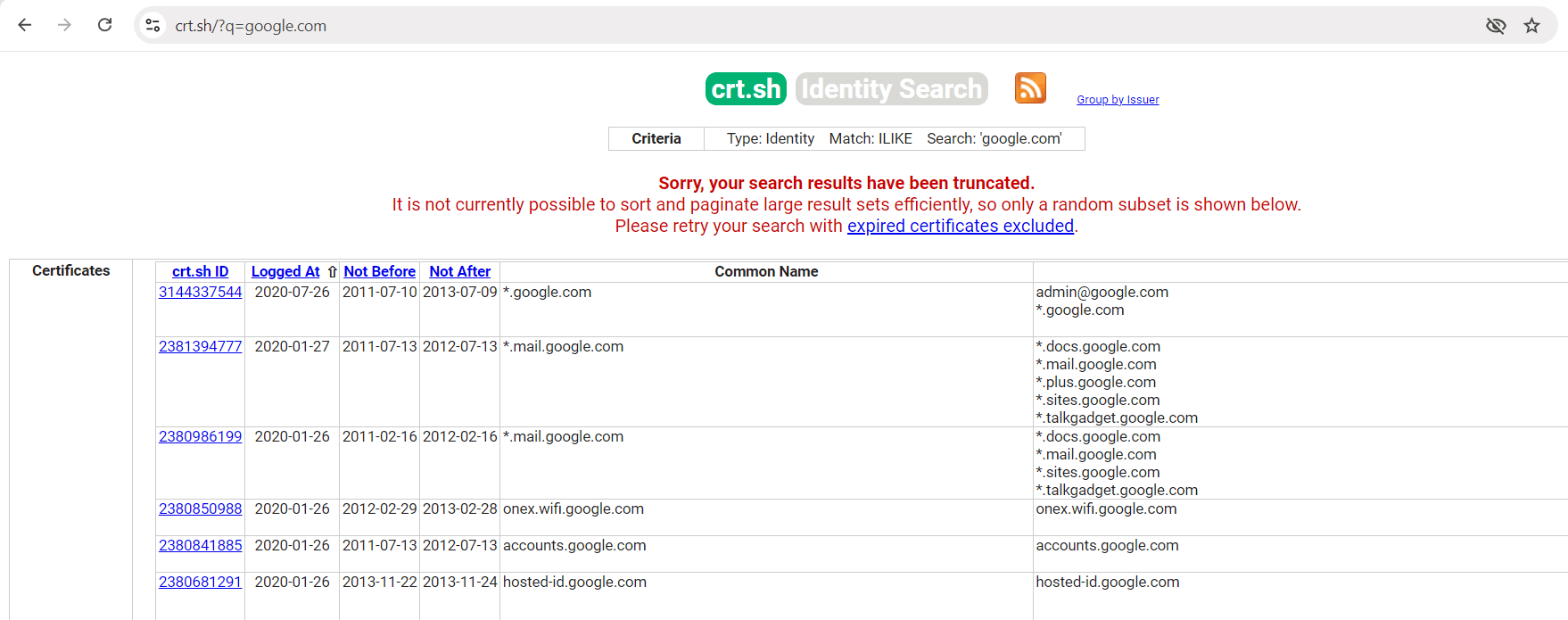
Installation of command line CRT.sh tool
I know this can be complex to do the copy all the subdomains and save into the txt file. So you can install the following command link tool that can help you to do the subdomain enumeration and bring all the output to the command line interface as shown in the image below.
Crtsh.py Github Tool.
Installation of Crtsh.py github tool
git clone https://github.com/YashGoti/crtsh.py.git ; cd crtsh.py ; chmod +x crtsh.py ; python3 crtsh.py -h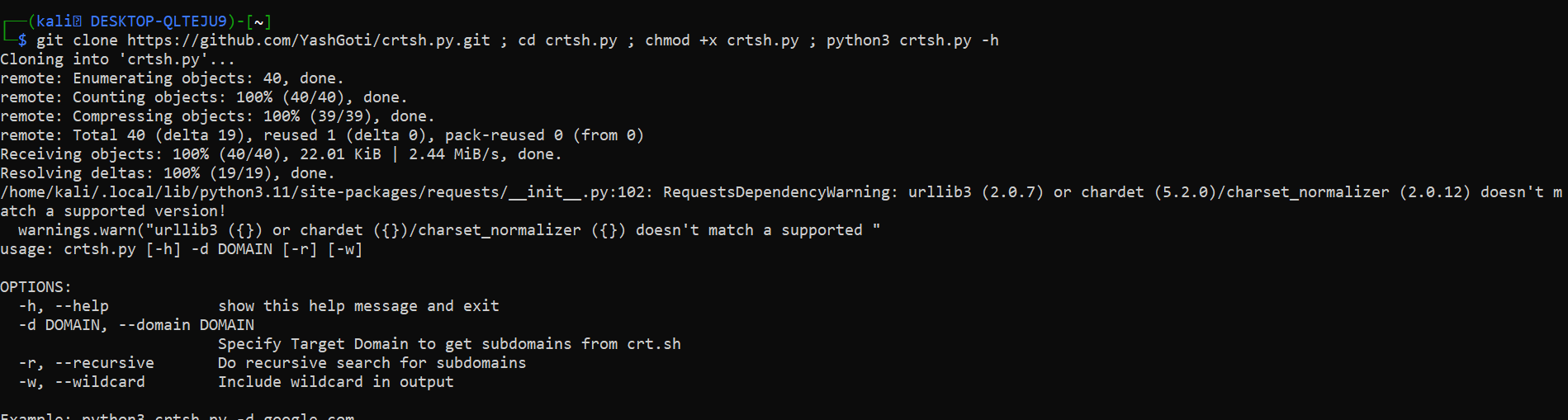
CRTsh Command
python3 crtsh.py -d google.com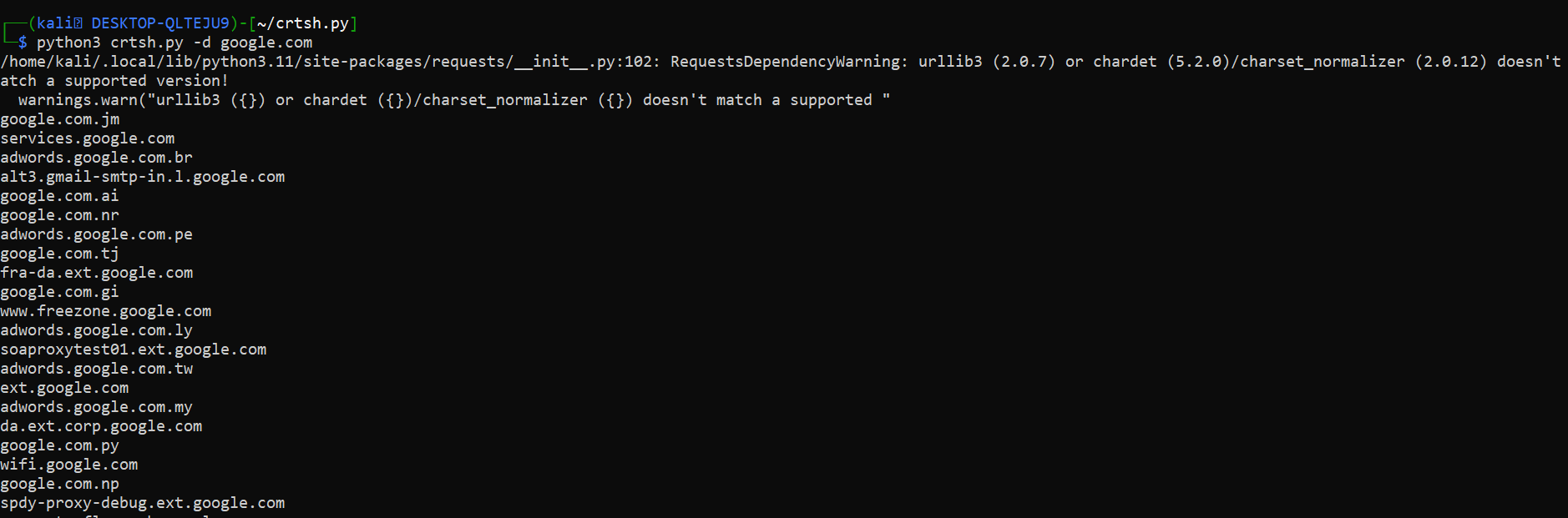
SecurityTrails subdomain
First, search the domain to see if it’s available. Then, navigate to the history section. Manually copy all the subdomains and IP addresses.
By using this method you will find some unique subdomain. Make sure you will do this method. This method is time consuming so most of the people SKIP. So you can use there laziness to your advantage and find some low hanging bugs/high bugs ;P
Thank You For Reading This Blog Post 😉
AND BY FOR NOW will meet soon in another blog post ;D
Btw, if you want some in-depth subdomain enumeration methods, you can read this blog “Master Subdomain HUNTING | Art of finding Hidden Assets“.
FAQ
What is subdomain enumeration
Subdomain enumeration is finding smaller websites within a main domain. It’s used in security testing. This helps find hidden or vulnerable parts of a website.